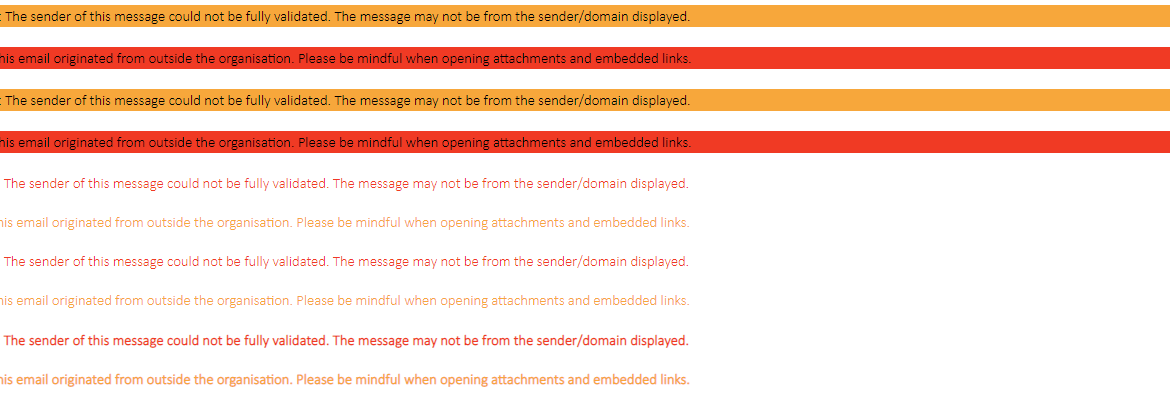
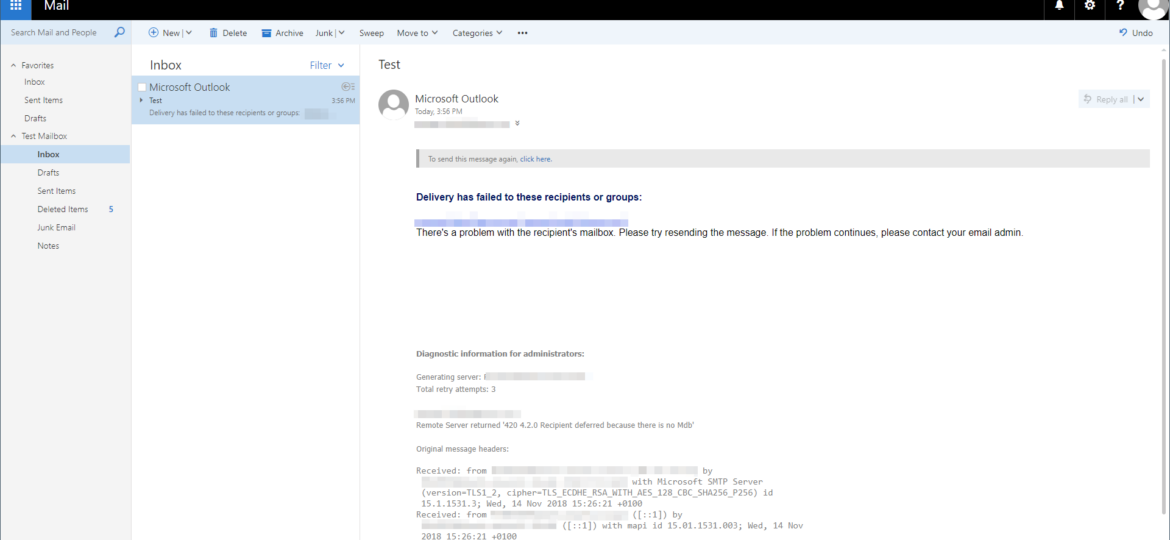
I’ve been managing mail service for users for a lot of years now. I don’t do it daily but I’ve spent my fair share of time analyzing spam emails. Mail vendors are doing what they can fighting spam, but it’s not easy. Each month, each year spam is getting more sophisticated. Spam emails either look like a legit email, or worse someone is targeting your company trying to get them to transfer money into a wrong account. While most of those end up in spam, there are those that come thru. It’s even worse if the company you work with has not implemented SPF or their SPF is configured to soft fail which can’t be treated as spam.
Office 365
One of the tasks I often get when setting up new Office 365 tenant or installing Exchange Servers is to change the visibility of Room Mailboxes or in some cases even standard users. There’s nothing hard about it, and there are plenty of articles about it. It’s just three simple steps.
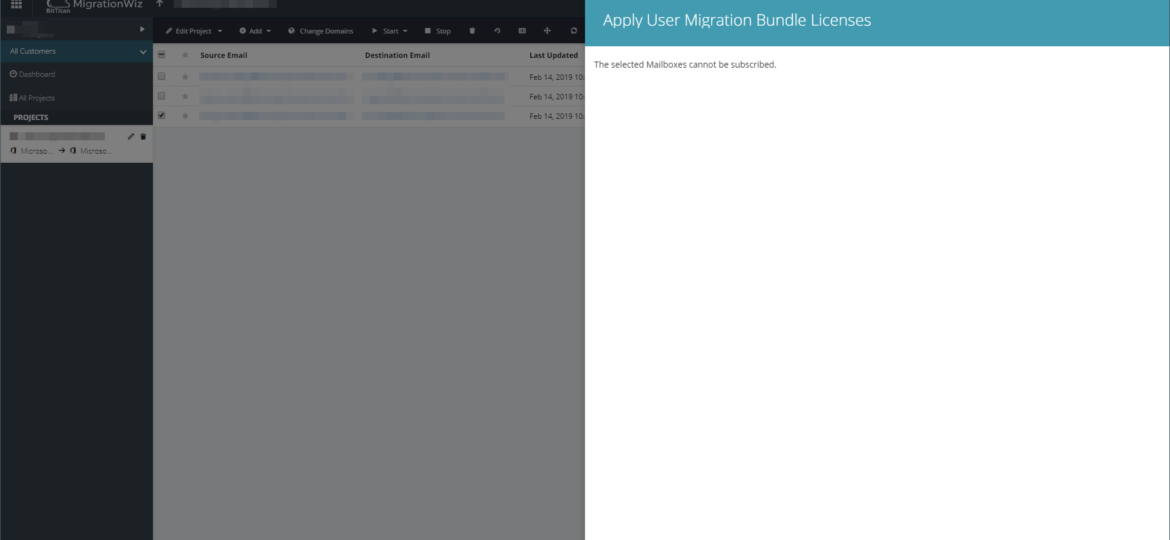
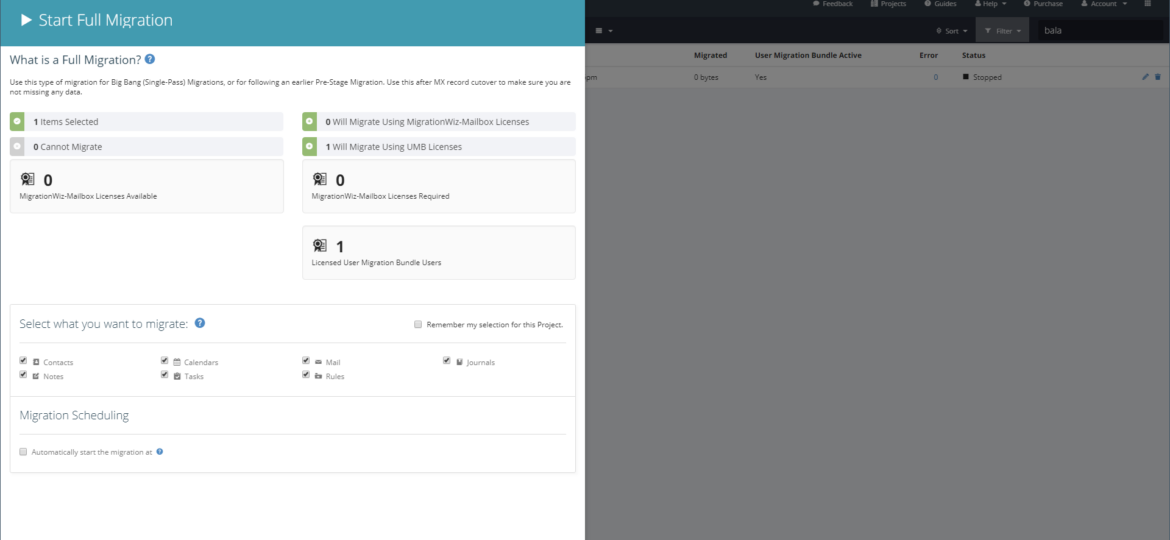
Recently I’m doing yet another migration between Office 365 tenants using Bittitan Migration Wizard. It’s a great tool and takes away a lot of headaches when dealing with the migration of mailboxes or OneDrive data. Unfortunately, like with many blogs on my website I had to hit yet another error. This time error occurred when I tried to assign User Migration Bundle license to users on the Migration Wizard.
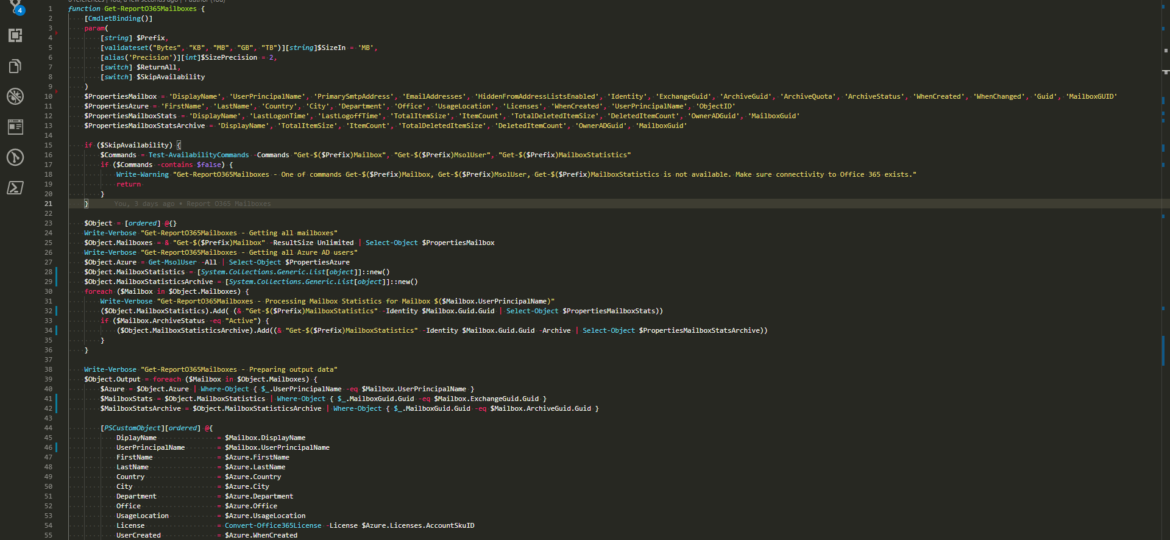
Working with Office 365 is my bread and butter in the last few months. I’m a System Architect and I am dropped in multiple projects, both new and old, to fix certain aspect and get out before anyone sees me. One of the common tasks I get is to provide some data about users stored in Office 365.
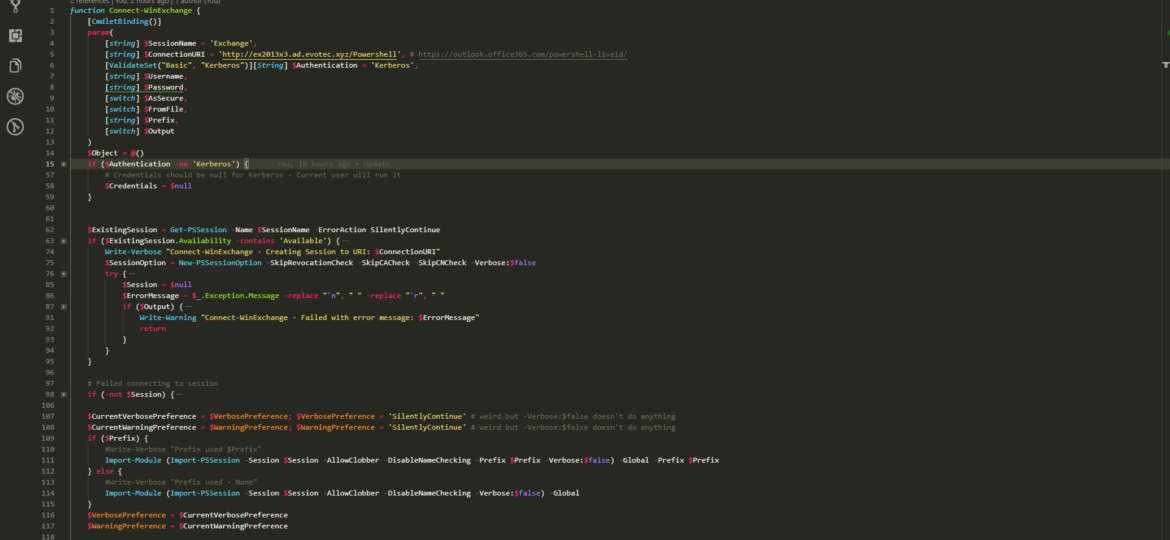
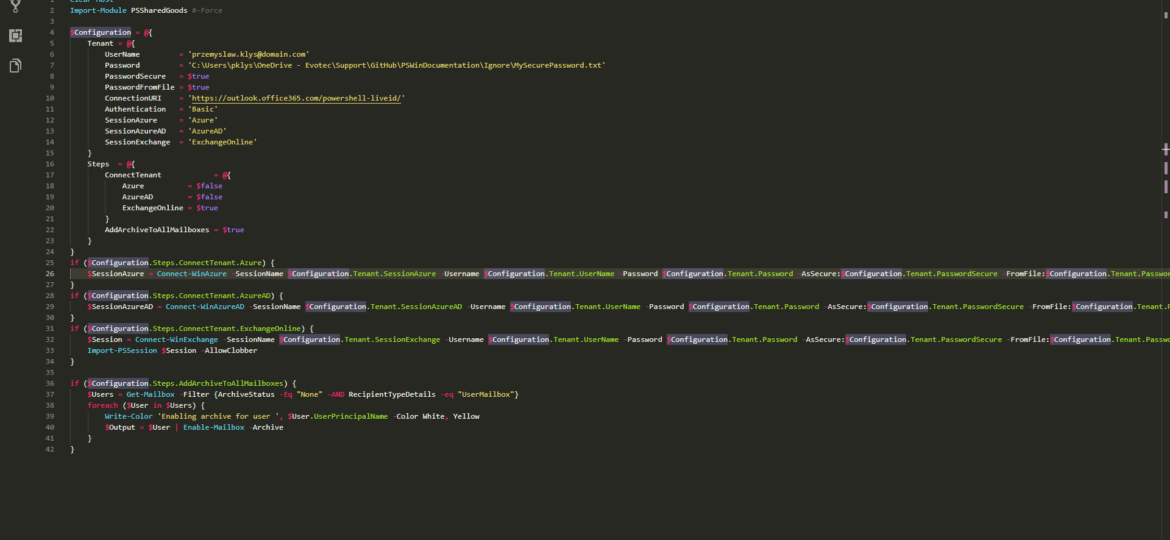
Last few weeks I’m responsible for migrating from Office 365 to Office 365. Part of this migration process is to set up new Exchange 2016 server that will work as relay instead of using IIS server. I’ve setup hybrid, added accepted domains, prepared connectors, but there’s one thing missing. Any time an email is sent via relay to a user that exists on Office 365 and at the same time exists in Active Directory email never gets there.
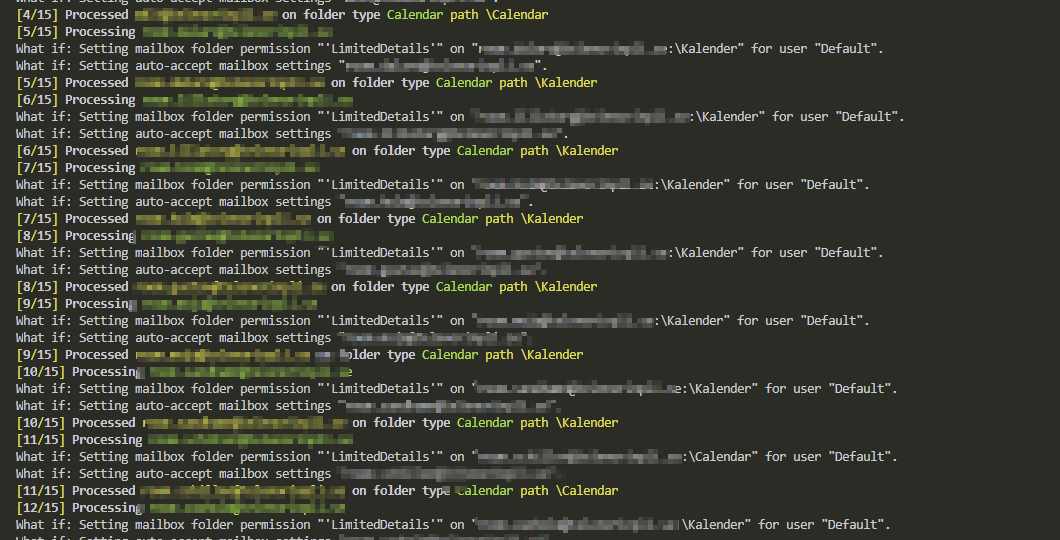
MigrationWiz from Bittitan is one of the best tools on the market allowing for migration of user mailboxes. Whether it’s a google account, exchange account or IMAP, it will help you out. Last few months I’m part of migration project that is using Bittitan at its core. One of the signature features of this tool is the ability to migrate mailboxes from Office 365 tenant to Office 365 tenant. This is not something that every application can do. Another feature (and something I want to address today) is the ability to ask users for their logins and password to migrate their data from one tenant to another tenant. While in general, you shouldn’t do that and you should use migration accounts with proper permissions sometimes you have no other choice.
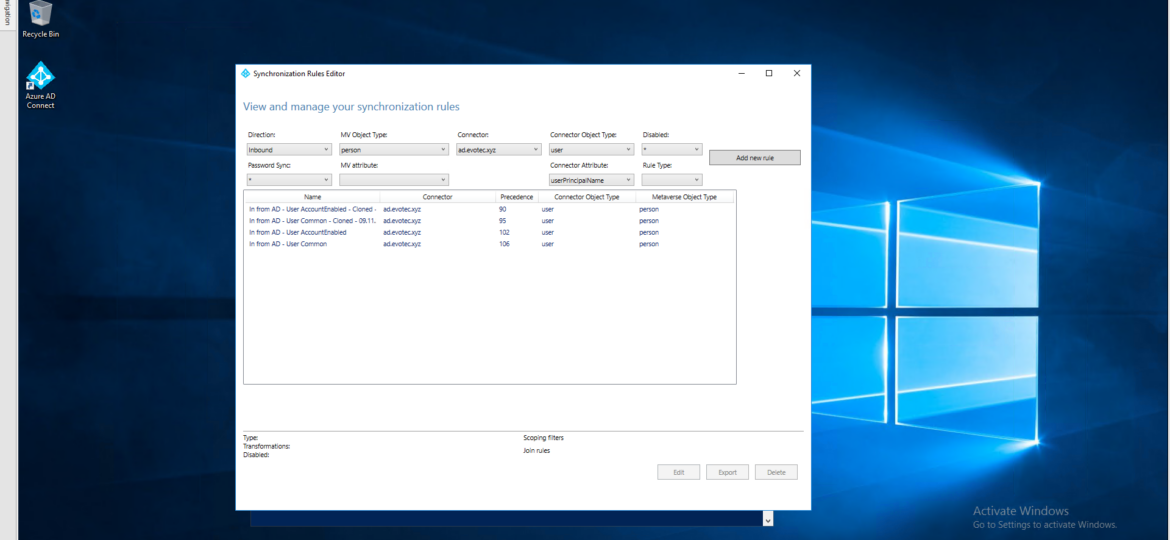
Azure AD Connect is an application responsible for synchronizing Active Directory with Azure AD allowing for a natural population of users, groups, and devices in Office 365. While for most companies standard setup is very easy and most of the time touch-free, there are companies which require greater customization. During installation of AD Connector, you choose what should be used for Azure AD Username from your AD. UserPrincipalName field is an obvious choice for this and also proposed by default for that purpose. This field is utilized further by your users to log in to your Exchange, SharePoint, Teams and so on.