I’ve been working on cleaning up Group Policies for a couple of months. While it may seem trivial, things get complicated when you’re tasked with managing 5000 GPOs created over 15 years by multiple teams without any best practices in mind. While working on GPOZaurr (my new PowerShell module), I’ve noticed that the more code I wrote to manage those GPOs, the more I knew passing this knowledge to admins who will be executing this on a weekly/monthly basis is going to be a challenge. That’s why I’ve decided to follow a similar approach as my other Active Directory testing module called Testimo. I’ve created a single command that analyses Group Policies using different methods and shows views from different angles to deliver the full picture. On top of that, it provides a solution (or it tries to) so that it’s fairly easy to fix – as long as you agree with what it proposes.
PowerShell
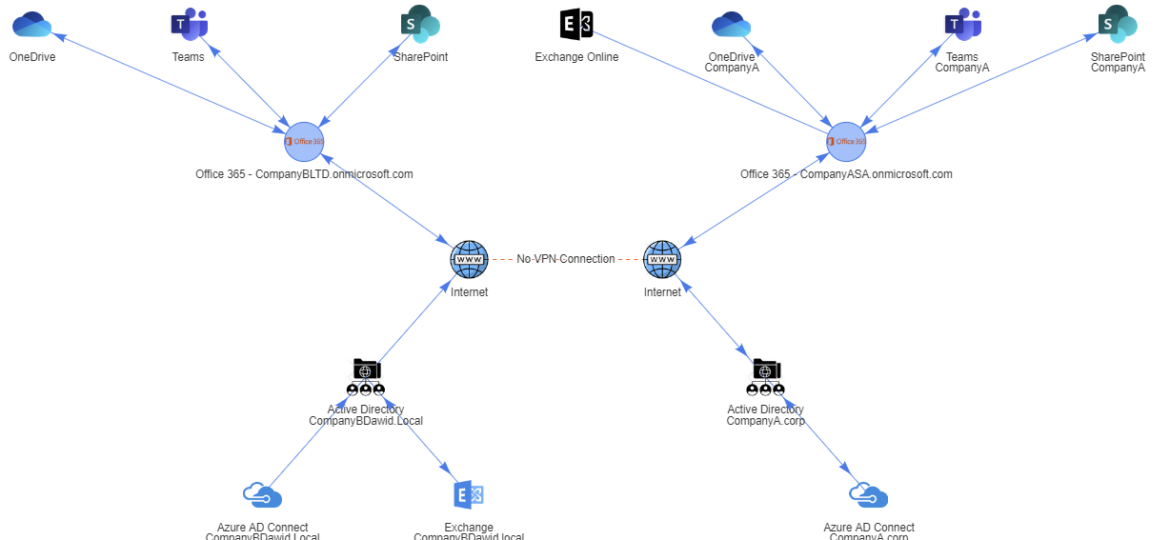
A few weeks ago, I posted a concept migration diagram for Office 365 to Twitter and Facebook. Today I thought I would show you how you can do it yourself using PowerShell and PSWriteHTML PowerShell module. When I started working on this, I’ve thought I want to create before and after infrastructure to see how it will look when migration ends. I’ve initially planned to assign myself an Office 365 Visio Plan 2 license and do something manually, thinking it may be just much easier. Unfortunately for me, there were no free Visio licenses in my tenant, and my laziness took over, so I’ve decided to give it a go using PowerShell only.
I like OneDrive. It allows me to keep my data secure and always synchronized. If things go wrong, I can always get it back. I use it for almost everything. Even for my PowerShell projects, which are committed to GitHub, so in theory, I shouldn’t need that. But every once in a while, I make some stupid mistake and delete a file that has yet not been committed to GitHub, and that’s where the OneDrive comes in handy. Quick restore, and we’re back. Unfortunately, sometimes things aren’t as I would expect them to work. For example, let’s have a look at this nice list of markdown files that are documentation for my module called GPOZaurr.
PSTeams PowerShell module has been on the market for a while now. It supports sending notifications to Microsoft Teams channels via Incoming WebHooks. You could send a pretty message to the team’s channel with just a few lines of code. With PSTeams 2.0, support for Adaptive Cards, Hero Cards, List Cards, and Thumbnail Cards was added.
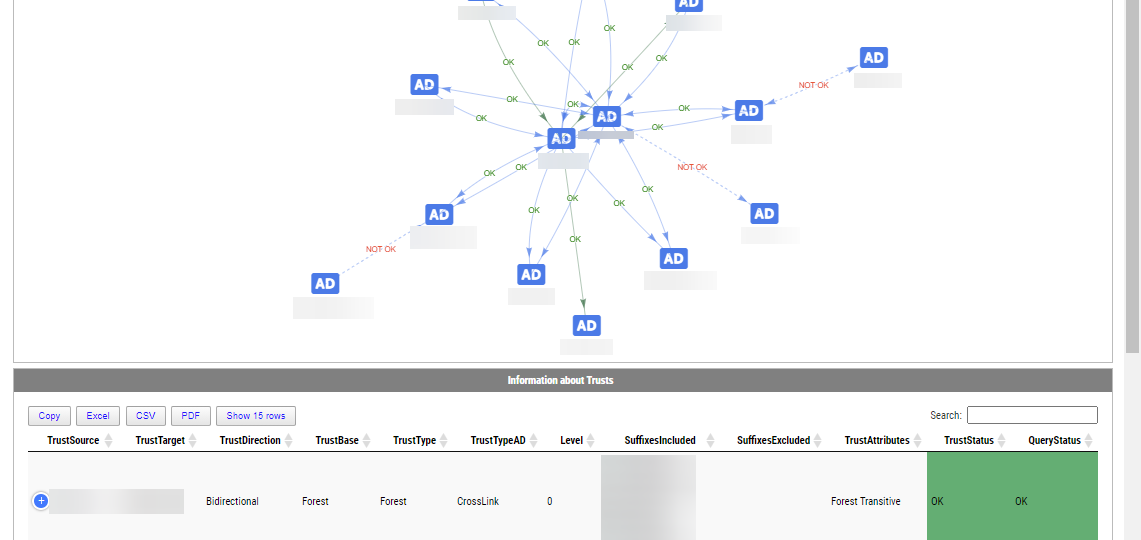
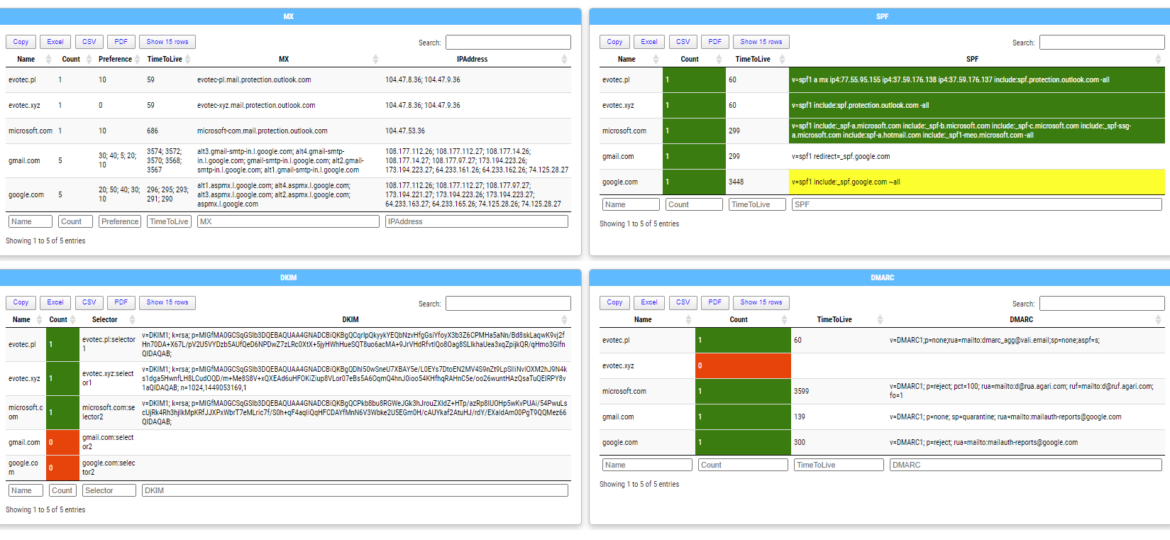
Active Directory Trusts are useful to connect one or more domains. But as useful those are, they can be very dangerous. Also, keeping trusts working and in good shape should be a top priority for Active Directory Admins. While there is a couple of command in the Active Directory module Get-ADTrust, I thought I would try and write my own that checks a few more things. I want to thank Chris Dent for his input on the part of this command. His binary skills amaze me!
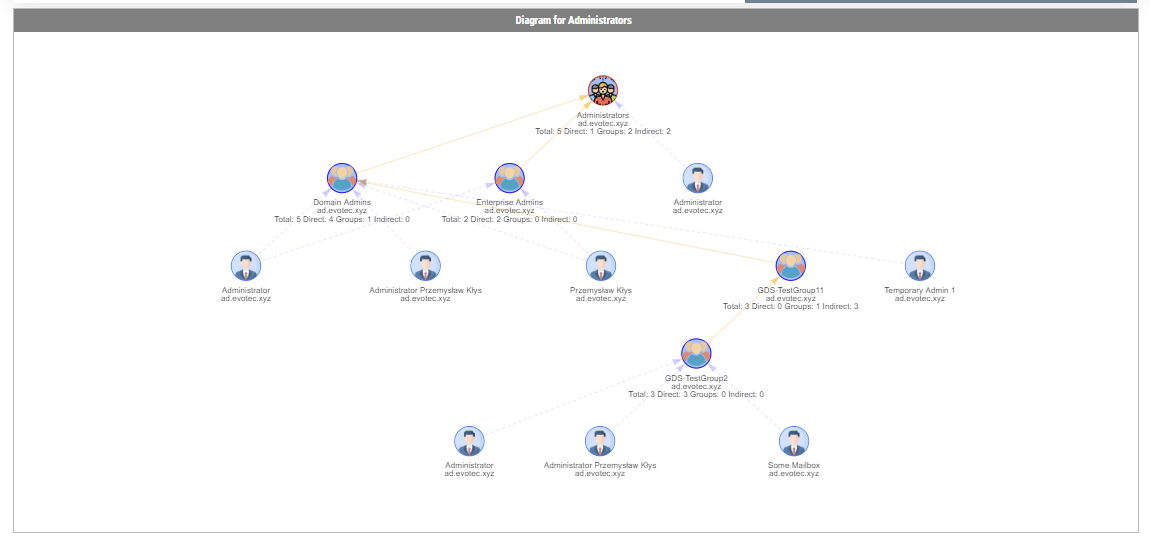
In the Active Directory PowerShell module, you have two commands to your disposal that help display group membership. Those are Get-ADGroup and Get-ADGroupMember. The first command contains property Members, which gives you DistinguishedName of all members, and Get-ADGroupMember can provide you either direct members or with Recursive switch all members recursively (skipping groups). Till a few weeks ago, I was a happy user of those commands until I noticed two things. Member property for Get-ADGroup sometimes misses elements for whatever reason.
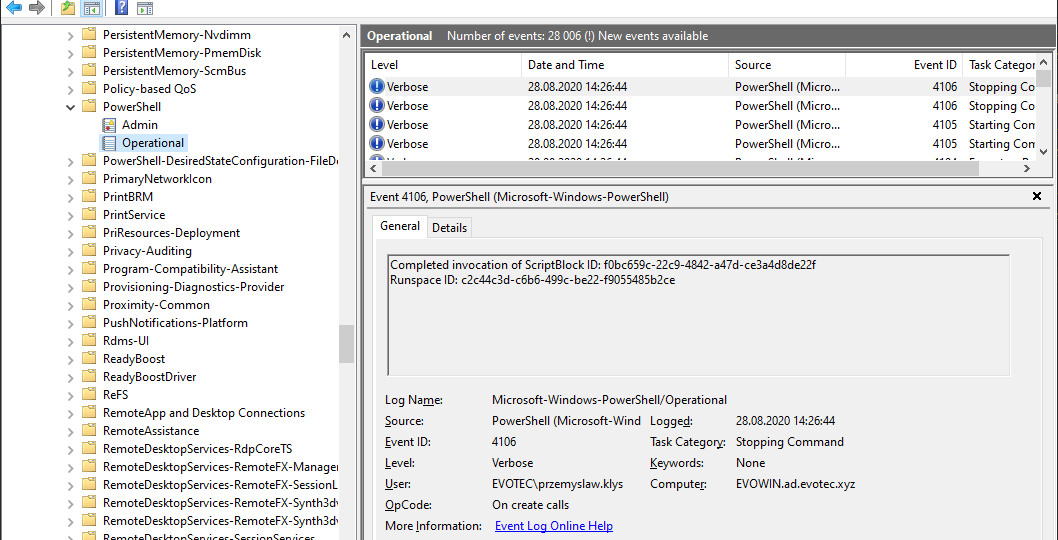
A few days ago, I was asked to take a look at PowerShell Malware. While I don’t know much about malware, my curiosity didn’t let me skip on this occasion, and I was handed over WindowsPowerShell.evtx file. Ok, that’s not what I expected! I wanted PowerShell .ps1 files that I can read and assess? Well, you play with the cards you were dealt with. What I was handed over was PowerShell Event Log. PowerShell writes whatever you execute, and it thinks it is risky, to Windows PowerShell Operation Event Log.
Today, I’m introducing a new PowerShell module called Mailozaurr. It’s a module that aims to deliver functionality around Email for multiple use cases. I’ve started it since native SMTP cmdlet Send-MailMessage is obsolete, and I thought it would be good to write a replacement that adds more features over it as things around us are changing rapidly.
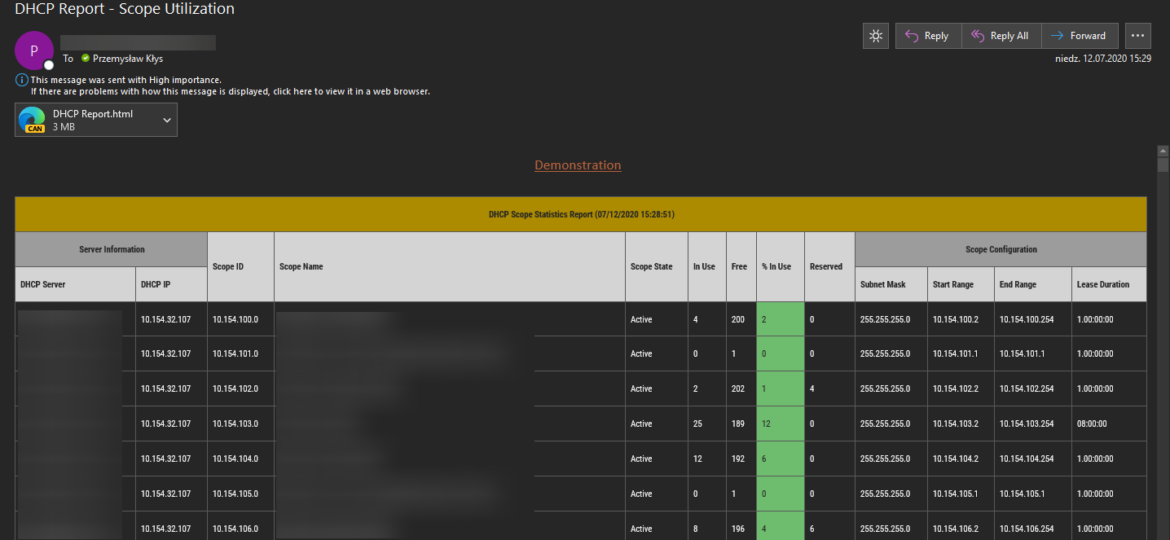
I’m pretty addicted to reading blog posts. I saw this new blog post the other day, where the author created the DHCP HTML report, and he did it by manually building headers, footers, table borders, and finally, adding some coloring to the percentage of DHCP being in use. It’s the „standard” approach to build HTML in PowerShell, and I’ve seen a similar path before, but that got me thinking how much time it would take for me to replicate the very same functionality using PSWriteHTML module.
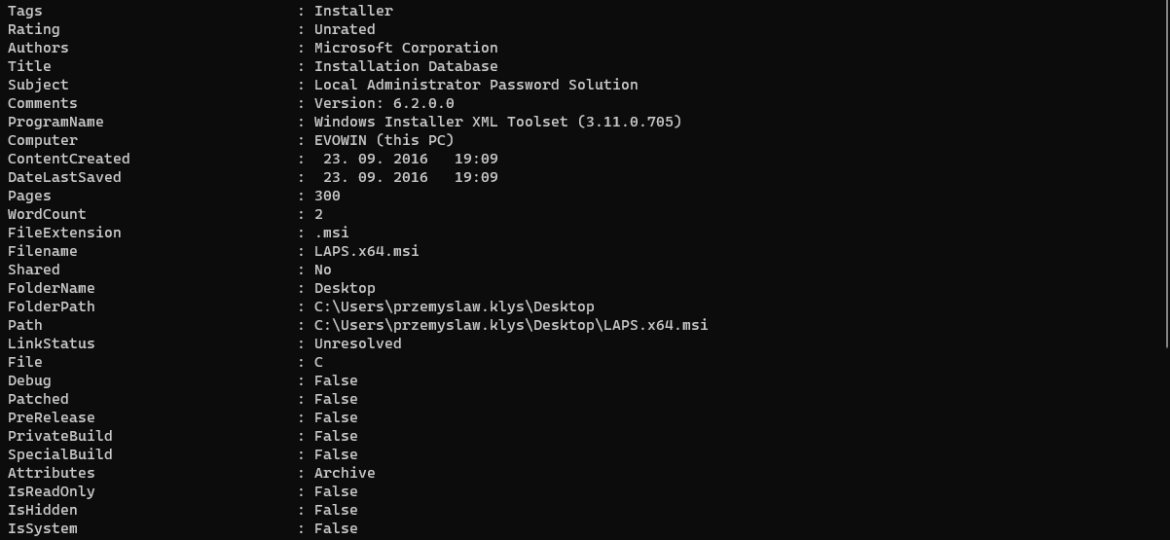
I’m working on a new feature for one of my modules that requires me to know what kind of files I am working with. It’s quite easy in PowerShell, and without a lot of code, you can reasonably quickly get necessary information about data stored on your desktop or anywhere else for that matter.