Working as Administrator with Active Directory can be rewarding. You can easily deploy new settings, make changes to users even on largest scope. Whether it's 10 people company or 100000 people company there are benefits on having Active Directory in place. One of the challenges for Active Directory is knowing how to monitor changes to it. While you may think that when you're lone wolf working as a main Administrator you don't need to monitor your Active Directory it may not always be the case. Things get even more complicated with more Administrators having access to your AD or Service Desk agents having some access rights to part of it. Recently one of our Clients asked us if he can receive daily, monthly and quarterly reports of changes that happens to users and groups. He is required by law to know if our Administrators are doing their job with proper procedures in place or they just run headless creating accounts and giving access to sensitive data. While there are many products on the market that can provide this kind of monitoring or even scripts that monitor Group Membership Changes like the one from Lazy Win Admin which I've initially used to try things out but they were lacking one small thing – who did the change and when.
Please notice this article contains parts of information (still useful) and may not reflect all functionalities of this module. For download, source code and so on you should refer to the dedicated PSWinReporting module page. After reading this one… of course! It contains useful information, examples and know-how.
💡 Comparison of monitoring changes
When monitoring your Active Directory you can take 2 roads:
Monitoring group and user changes by saving the data before and after the change and doing comparison
Monitoring security events on your Active Directory controllers
Both have their pros & cons and from what I've seen on the Internet there are many options to monitor it the first way, but then you lack some of features.
💡 Solution
Following solution requires 4 parts for optimal reporting:
Enabling Event Logs to store proper Security Events
Enabling Event Logs on Domain Controllers to store more data (Security logs grow quite fast)
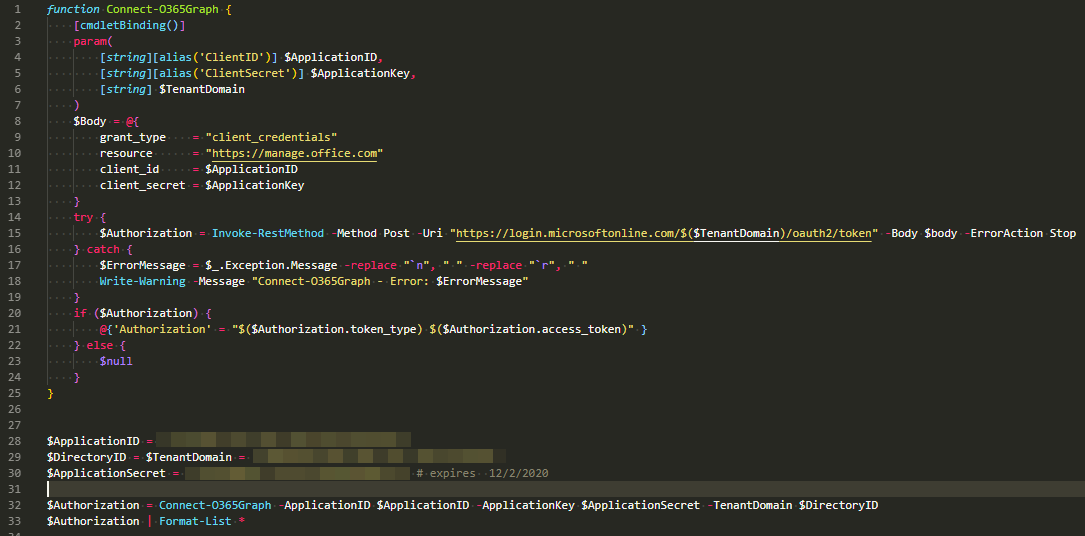
Setting up PowerShell Script (attached below) as Task Schedule (Get-EventsLibrary.ps1).
Running as Domain Admin Service Account (I know – not optimal) or having delegated access to Security Logs (not a trivial task to achieve)
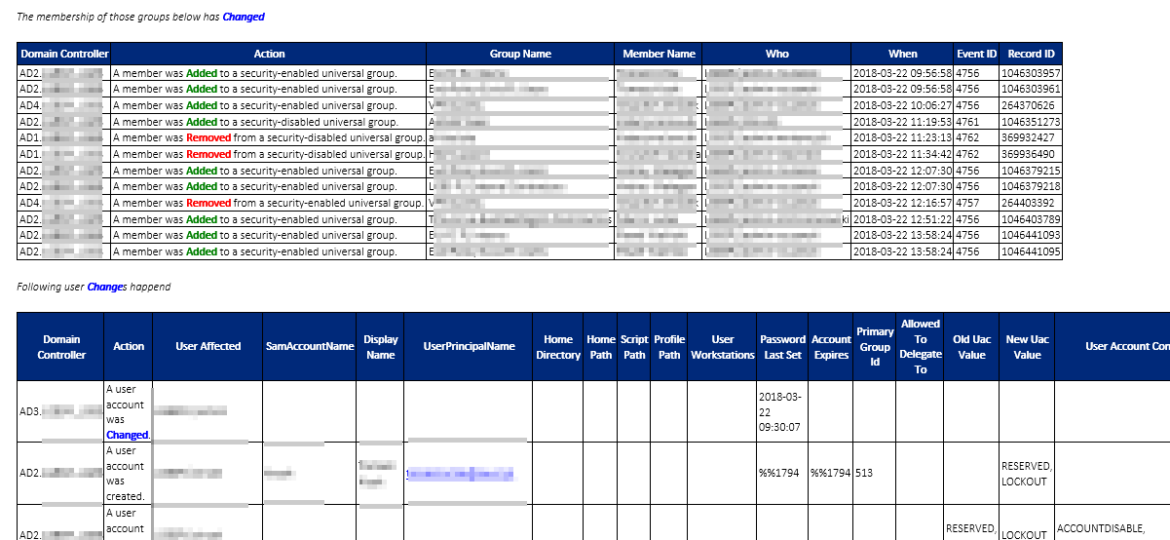
This PowerShell script can generate report according to your defined parameters and monitor for changes that happen on users and groups in Active Directory. It can tell you:
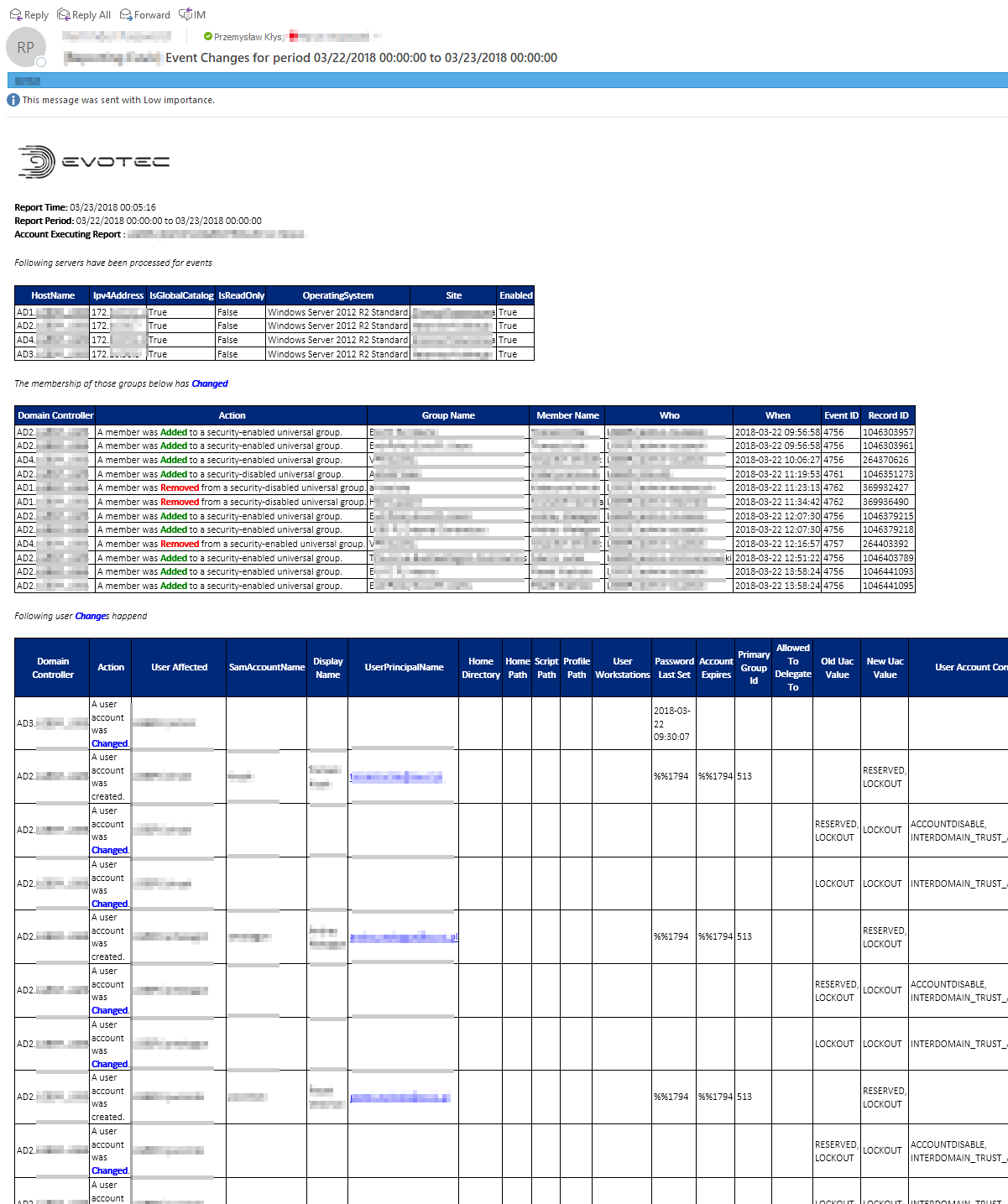
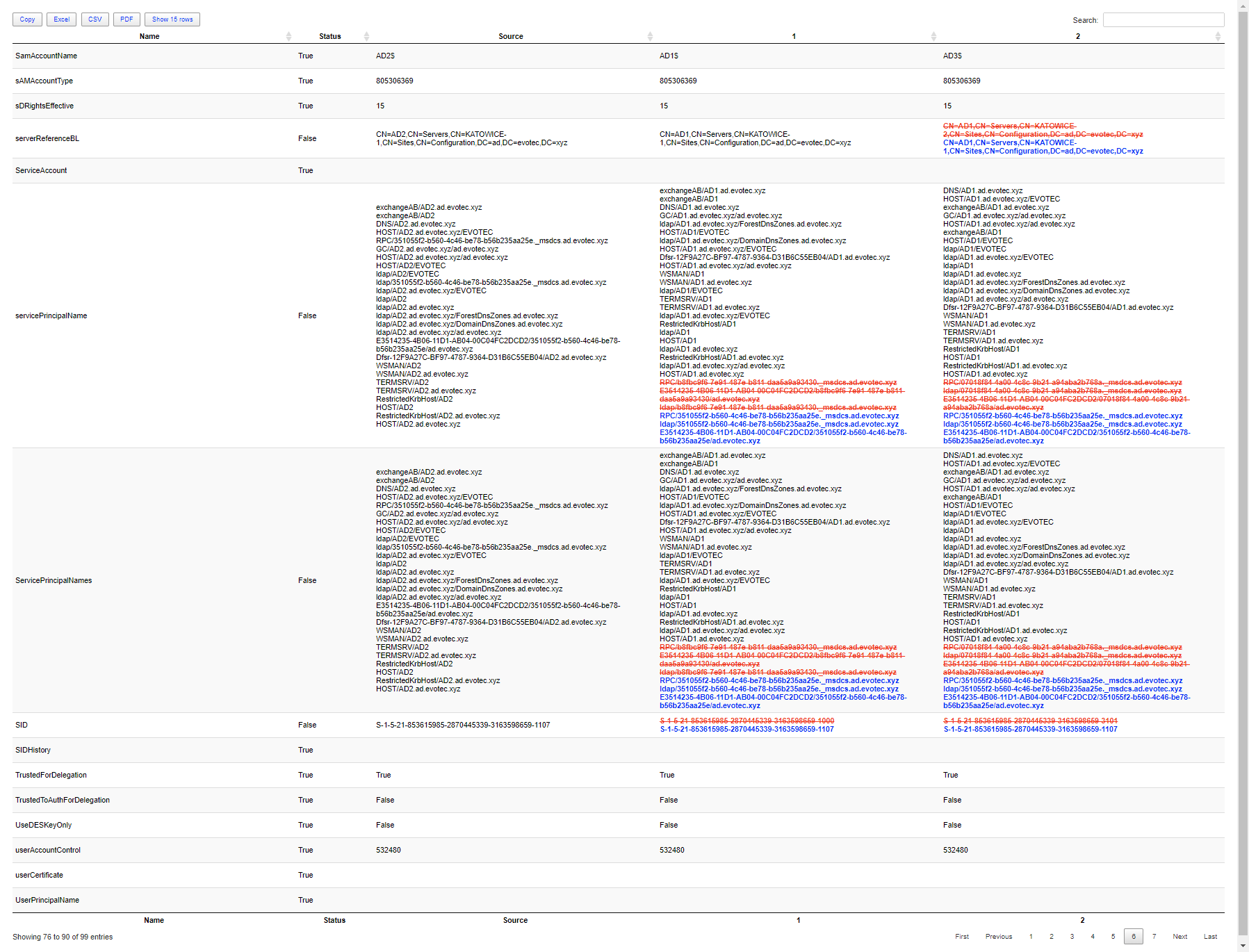
When and who changed the group membership of any group within your Active Directory Domain
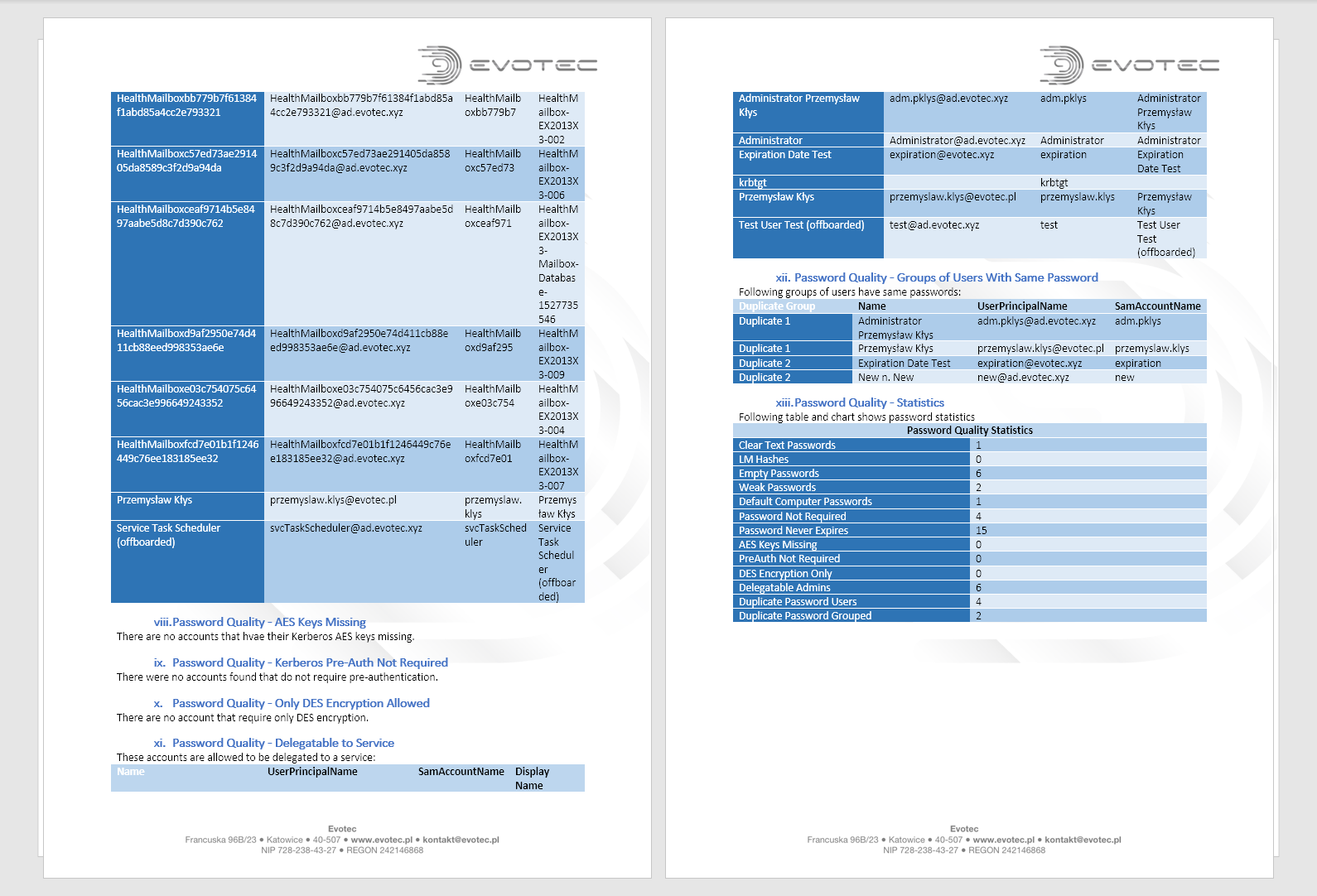
When and who changed the user data including Password, UserPrincipalName, SamAccountName, and so on…
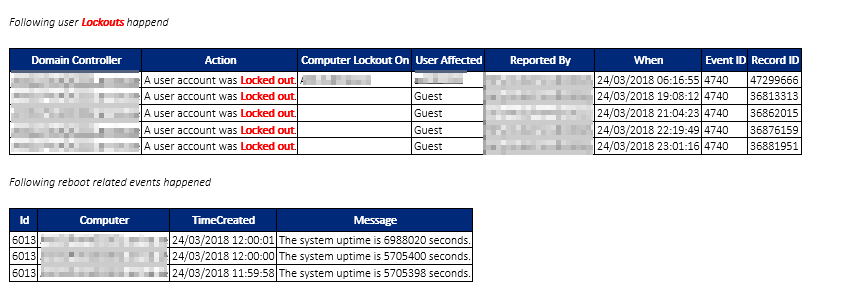
When and who changed passwords
When and who locked out account and where did it happen
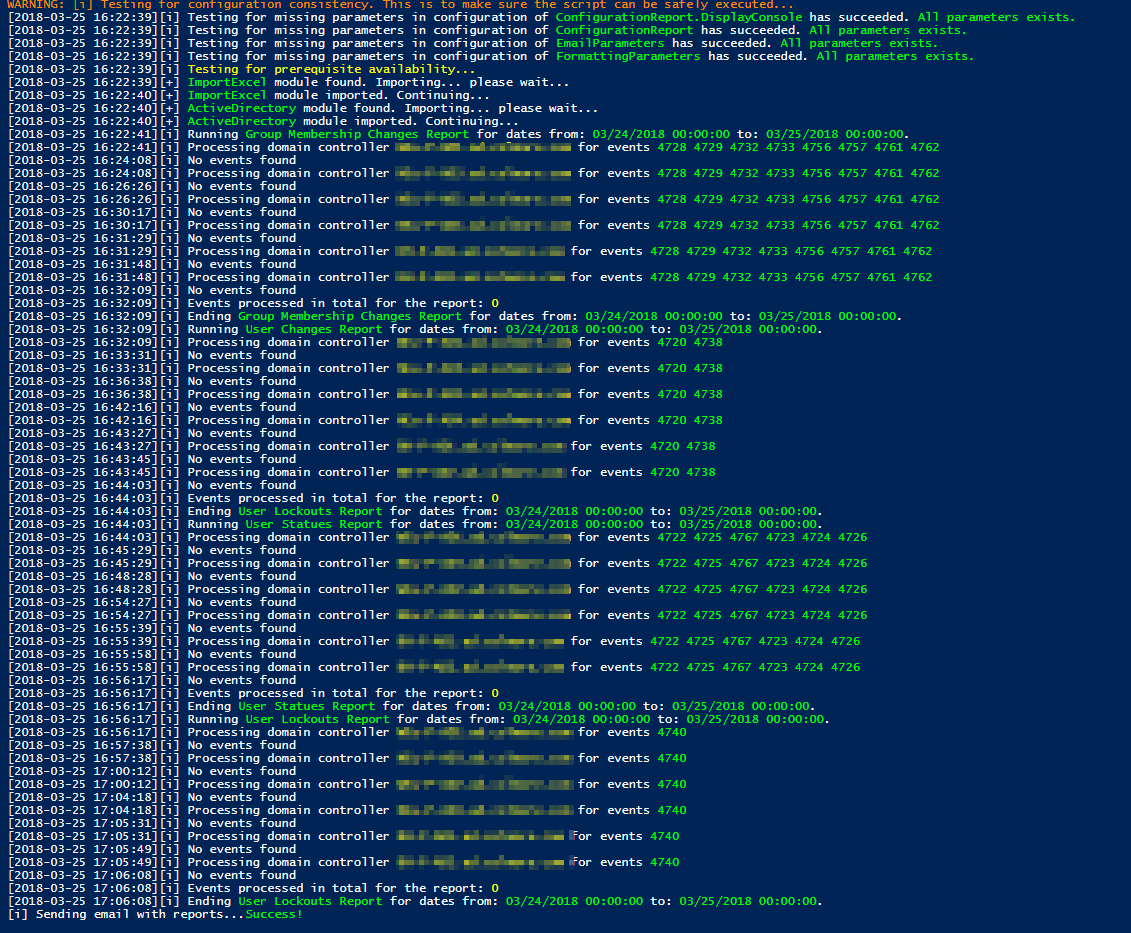
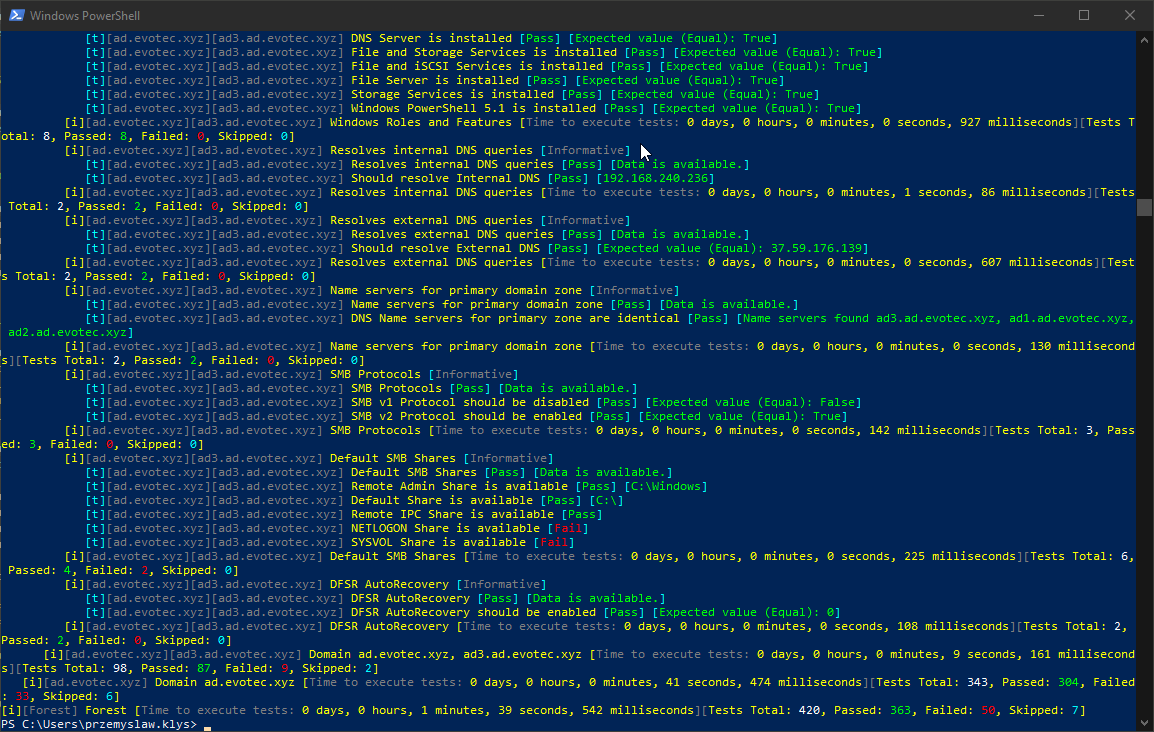
When you run the script following screen shows up. It means it's running. Please notice it can take a while to do the scan depending on the size of your environment.
When it's done you will get an email with some nice layout of information. You can find a sample report generated by the script. I have removed some bits and pieces but it should give you a brief overview of what you get. Best of all it's free.
And several others
This solution consists of 2 scripts. So called configuration and starting script (Get-Events.ps1 – you can call it however you like thou) and the real deal Get-EventsLibrary.ps1 that does the heavy lifting. The idea behind splitting those 2 scripts, instead of using just one, is so that configuration file can store all the confidential data and the library can be easily replaced with new versions when they come out without need to edit and potentially affect deployment.
Recommended approach:
Run it daily via Task Scheduler on 00:05 for the past day
If you set it up to run daily on 00:05 and set options for ReportPastMonth = $true it will send additional report on 1st of each month with requested data
If you set it up to run daily on 00:05 and set options for ReportPastQuarter = $true it will send additional report on 1st of each quarter with requested data
Set your own company branding, adjust company logo, font size and so on
Do not edit Get-EventsLibrary.ps1 as I intend to add features / fix bugs which then you can simply drag & drop into your setup (that's why you've got the branding part covered in config setup)
You can find full code and additional description on how to configure this code on Get-EventsLibrary.ps1 page.