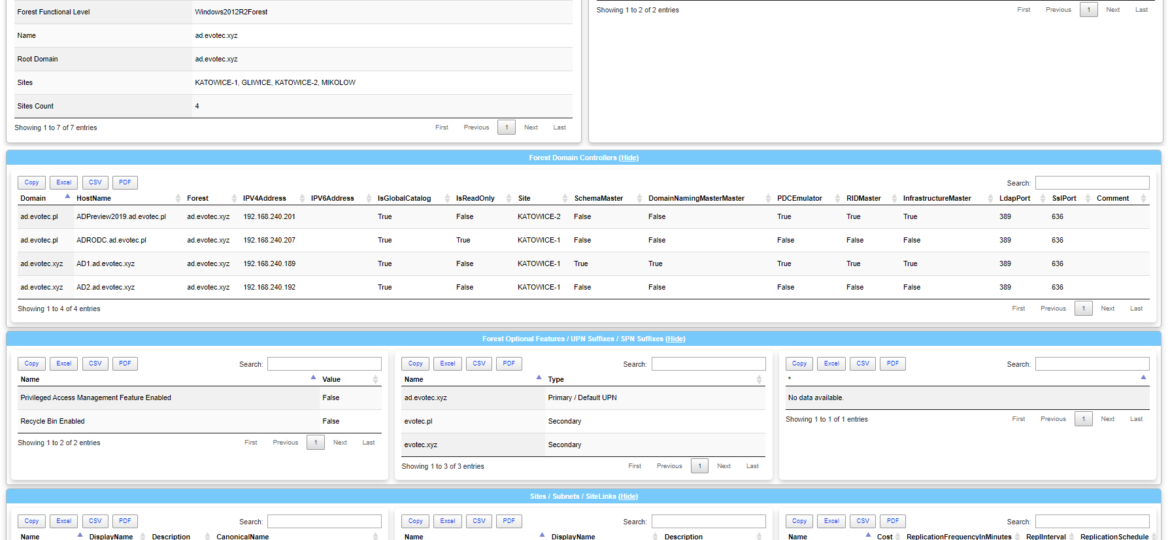
It’s no secret that nobody likes creating documentation. I don’t like it, and you don’t like it, even documentation lovers don’t like it. But while you can live without documentation, you really shouldn’t. And I am not talking here only about documentation that is only useful in the onboarding process of new employees or documentation concerning introducing someone to some concepts to get them easily start. I’m talking about documentation for your live environment where you know what you have, how you have set it up, but is still the same after one week, one month, or one year? Usually, not so much. And one of the worst mistakes admin can do is assume that his environment doesn’t change, things are as they were when they were set up.
powershell
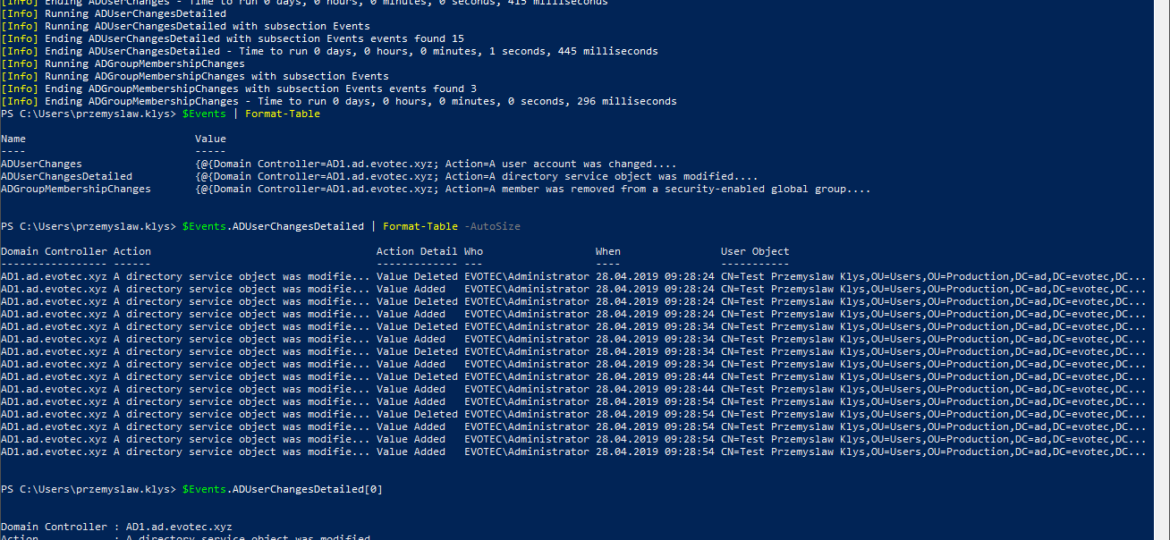
While the title of this blog may be a bit exaggeration, the command I’m trying to show here does it’s best to deliver on the promise. What you’re about to witness here is something I’ve worked on for a while now, and it meets my basic needs. If you don’t have SIEM product or products that monitor who does what in Active Directory this command makes it very easy, even for people who don’t have much experience in reading Event Logs. If you’d like to learn about working with Windows Event Logs here’s a great article I wrote recently – PowerShell – Everything you wanted to know about Event Logs and then some.
Recently there was this discussion on PowerShell Group on Facebook about issue posted by one user. While the subject doesn’t matter for this post, few people commented on the idea that he was using Format-Table in the middle of the pipeline to do something. They all said Format-Table should be used as last in the pipeline. Otherwise, you would get the wrong output. But should it? Well, it depends!
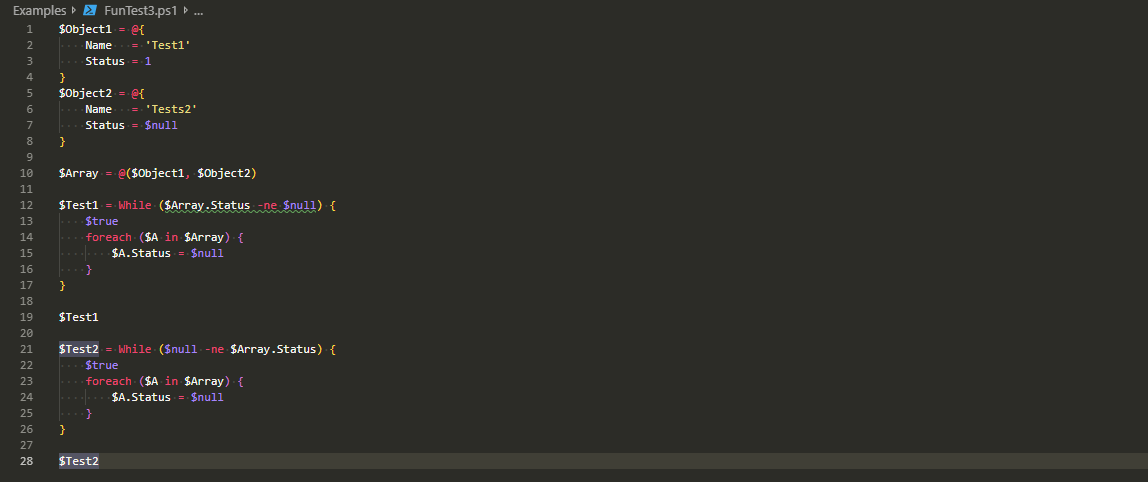
If you’re using VSCode with Powershell extension, you probably got used to PSScriptAnalyzer giving you all kind of tips on optimizing things. It makes your code better. Chris Bergmeister does a great job working on it. One of the tips PSScriptAnalyzer gives you when you use $null on the right side of the comparison.
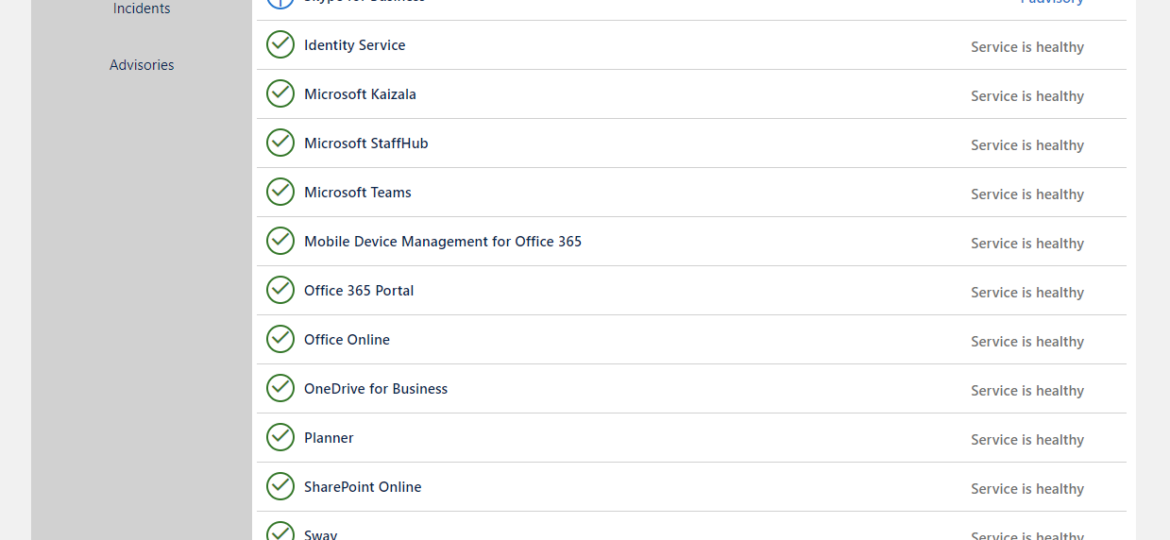
As you may have seen in my other post, there’s a simple, PowerShell way to get Office 365 Health Service data for you to use any way you like it. But before you can use that, you need to register granular permissions on your Office 365 tenant so that that data is provided to you. Here’s a step by step way to do it.
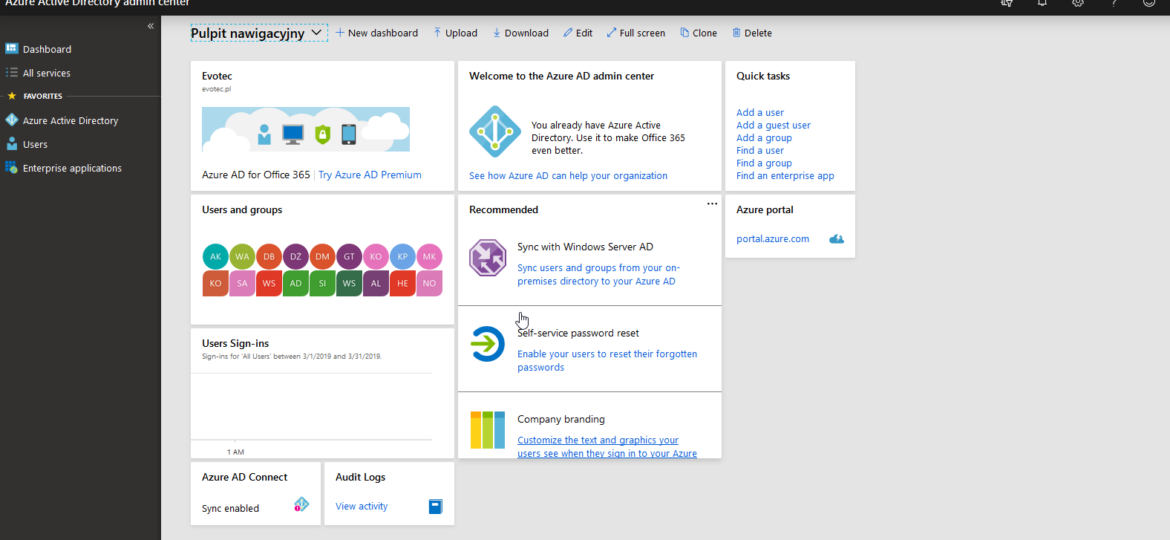
Office 365 is an excellent cloud service. But like any service, there’s some infrastructure behind it that has to be cared for. Since this is Cloud, Microsoft does this for you. But any problems Microsoft has to have some impact on your end users. And you may want to have that visibility for your users. Microsoft provides this to Admins when they login to the portal, but while useful you may want to use that data in other ways than those planned by Microsoft.
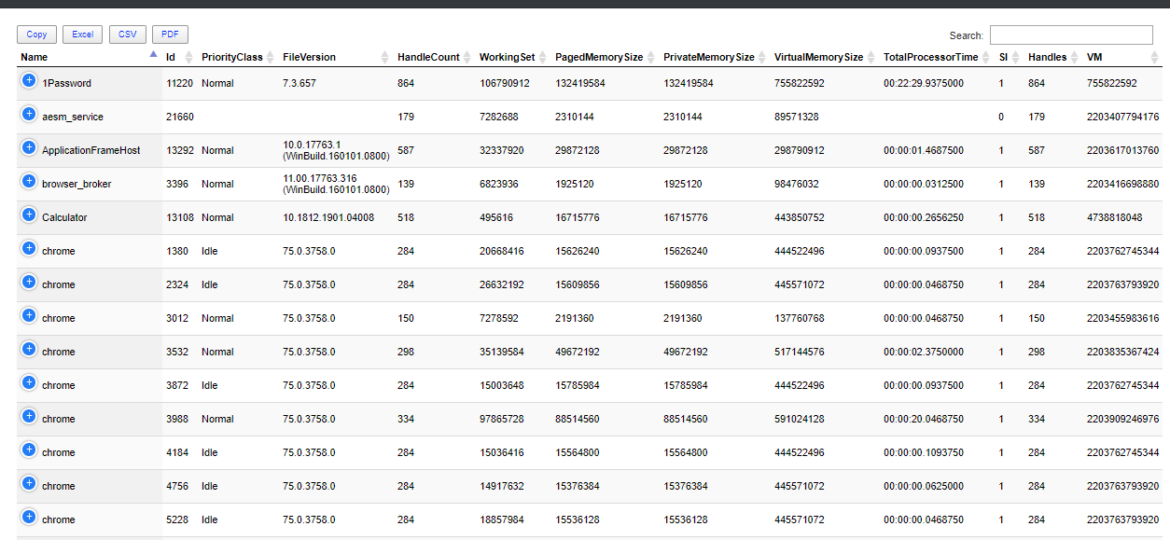
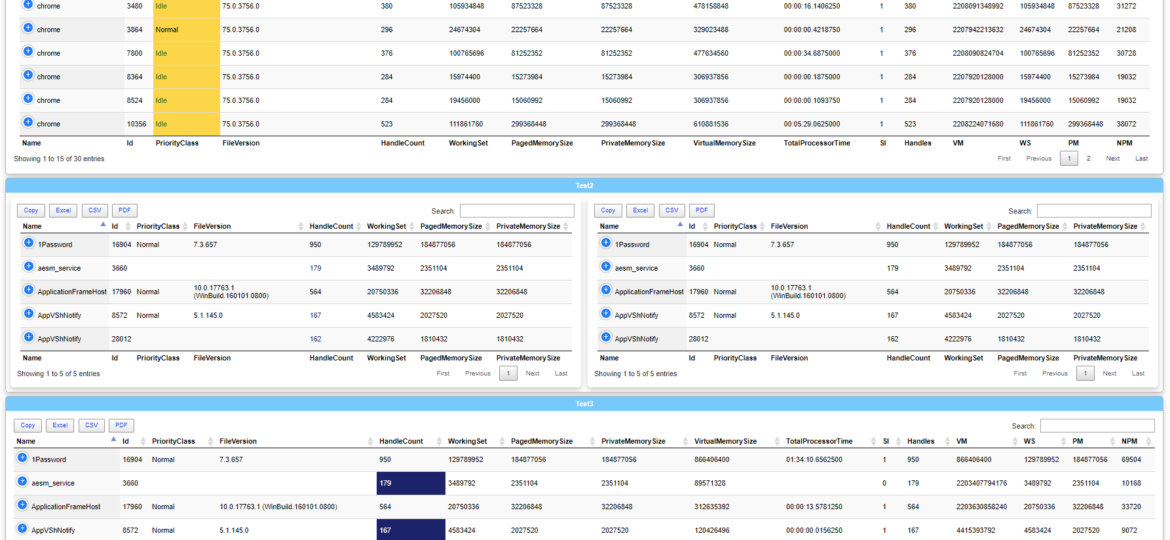
One of the most comfortable output’s in PowerShell to work and analyze data is Out-GridView. It’s handy as you can search, sort and have things done quicker than trying to do things in the console. However it’s currently not available in PowerShell Core (PowerShell 6+), and when it is available in PowerShell 7, it will NOT be cross-platform. Since I had released Dashimo a few days ago, I thought it was trivial to make a simple command out of it that could solve this problem.
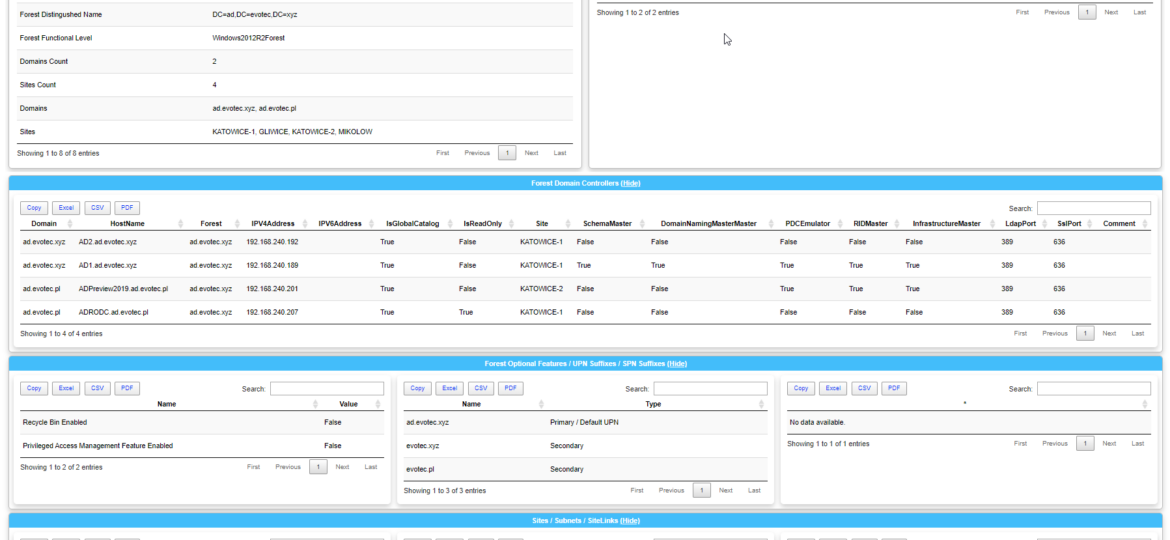
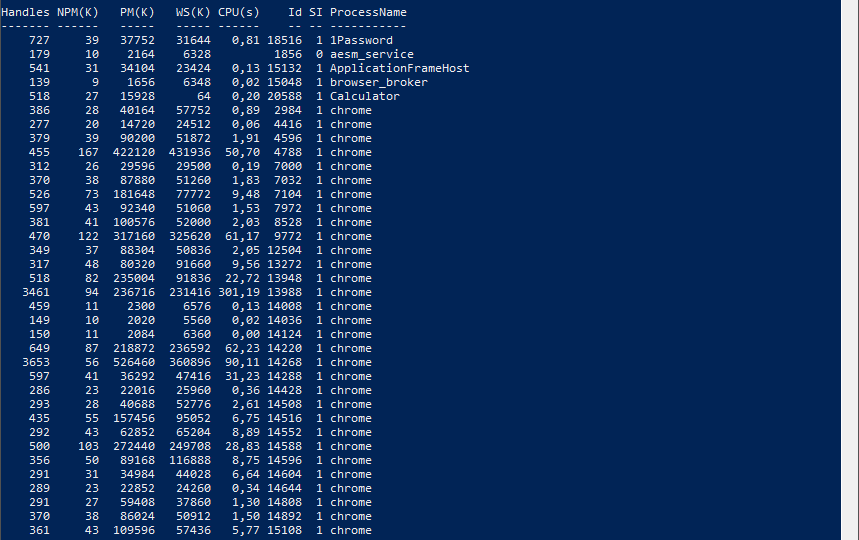
Dashimo ultimate goal is to be as easy to use as possible. With the introduction of it a few days ago I made a promise to myself that I want to keep it as simple to use as possible. If you don’t know what Dashimo is, have a read here – Meet Dashimo. When I posted it on Reddit few people had some ideas and feature request that would make it a bit nicer, and when I heard about I agreed. So today, after a couple of days I have a few updates. I also noticed that my examples might have been too hard to use and understand for beginners and people not having a lot of touch with Active Directory. This time all code you can find below will use Get-Process as a way to show you that you can use any output that comes as a Table.
Today I wanted to introduce a little product that I’ve created in the last few weeks called Dashimo. It doesn’t cover everything I wanted from it (feature wise), but it already can be used in production. Therefore, I thought it would be a good idea to get some feedback on whether I should spend some more time on it or throw it in the dumpster. Dashimo joins it’s older brother Statusimo of PowerShell modules allowing an easy way to build HTML output. If it will feel familiar, it’s because it was inspired with Bradley Wyatt PowerShell script he did. It gave me the idea of how I would like to build something similar but in a bit different way then he did, with much more flexibility. Still, if it wasn’t for him, the idea wouldn’t be there, therefore you should send him your thanks.
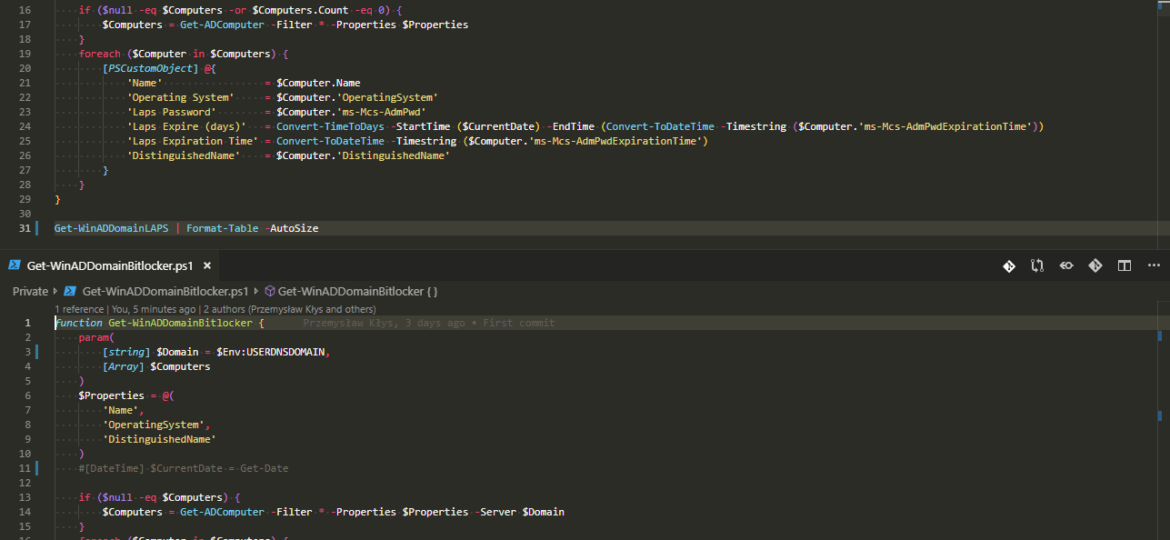
Having a modern, secure infrastructure in 2019 is a requirement. You should implement BitLocker to make sure that in the event of stolen laptop data is not readily extractable and implementing LAPS is a must in a fast changing IT world. But I’m not here to convince you to those two security features. I’m here to show you an easy way to backup LAPS and BitLocker. While having everything stored in Active Directory is excellent, things can get complicated when you don’t have access to your Active Directory, or you restore an older version of it. You see, LAPS, for example, keeps only last Administrator password. This is great and all but what happens if you restore the machine from backup from 6 months back? Your password has already changed multiple times. During our testing of DR scenarios, we wanted to access the computer via their local Administrator credentials and we just couldn’t because that password was already gone.