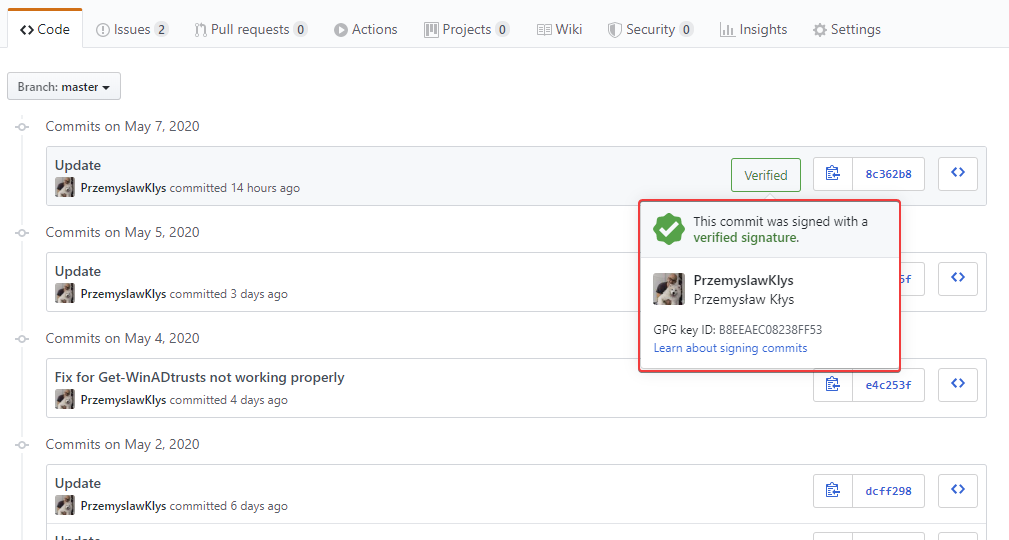
A bit over two years ago, I started posting my PowerShell code as modules on GitHub. Initially, I planned to have them hosted on my website, but few people asked to post it there, and they were right. It would be fairly hard for me to keep my code up to date on my website and, at the same time, let people submit bug reports or help with some PR. It was the right decision! Now that I’ve worked for over two years on GitHub as a daily driver, I wanted to get a new green badge that’s shown on GitHub when you edit some code. I don’t know if you ever noticed, but if you write any code, text file directly via the GitHub.com webpage, your commits always have Verified badge next to them.
powershell
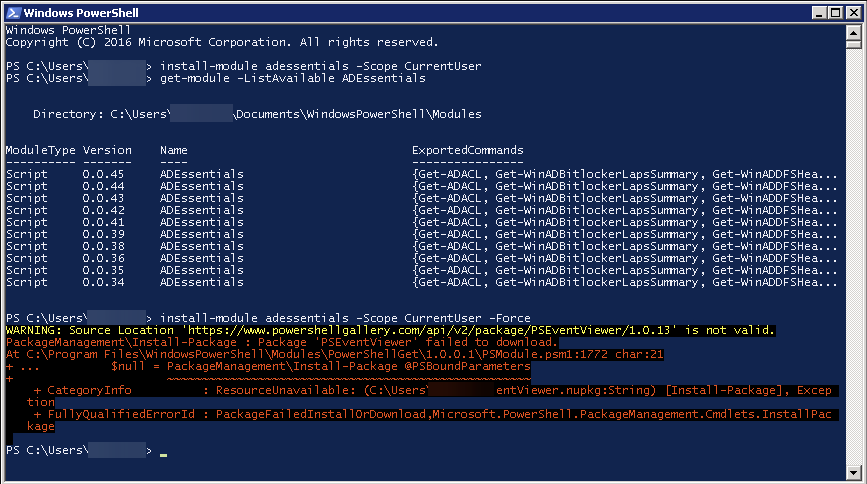
A few days ago, I tried to use Install-Module on the old Windows 2008R2 system that I use for specific tasks.
Office 365 has a lot of options and applications to choose from. Enabling one E1, E3, or any other license gives the user a lot of features, including Exchange, SharePoint, and Teams. But what if you want to make sure that the user can access only Microsoft Teams? By default, you can do it manually during the assignment of the license. Simply choose only Apps you want to assign to a user.
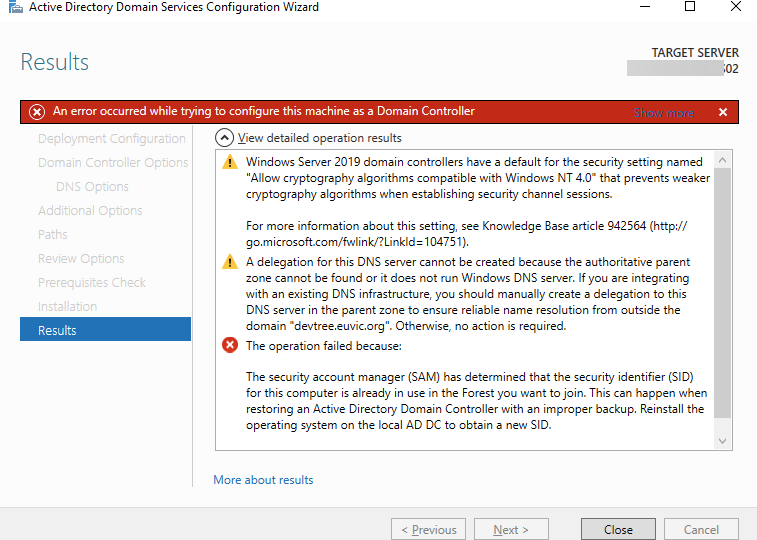
The security account manager (SAM) has determined that the security identifier (SID) for this computer is already in use in the Forest you want to join. This can happen when restoring an Active Directory Domain Controller with an improper backup. Reinstall the operating system on the local AD DC to obtain a new SID.
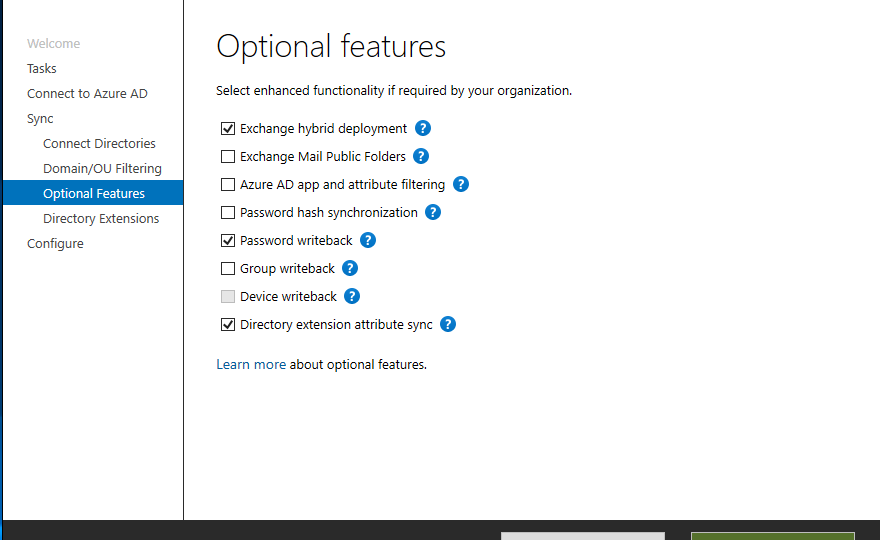
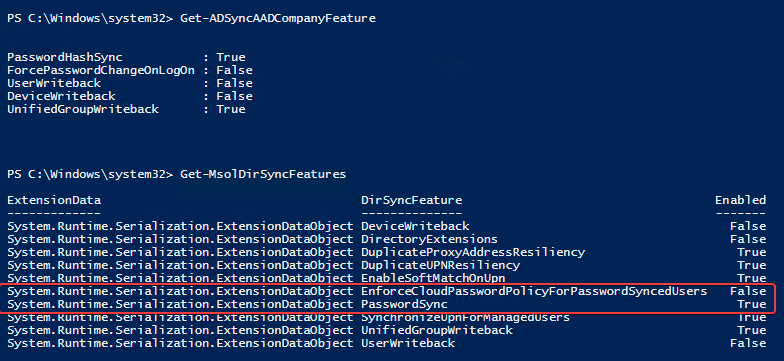
Azure AD Connect allows three ways to make sure the user password is the same in Active Directory and Office 365. Those are Password Hash Sync, Pass-Thru Authentication, and ADFS. While my preferred option to go with would be Pass-Thru Authentication, only Password Hash Synchronization is the easiest and least resource-intensive. It synchronizes user password to Office 365, and even if your Active Directory is down, you can still log in to Office 365. It’s perfect for small and even more significant companies that don’t have resources or can’t guarantee that their infrastructure will stay 100% time online so users can authenticate based on their Active Directory.
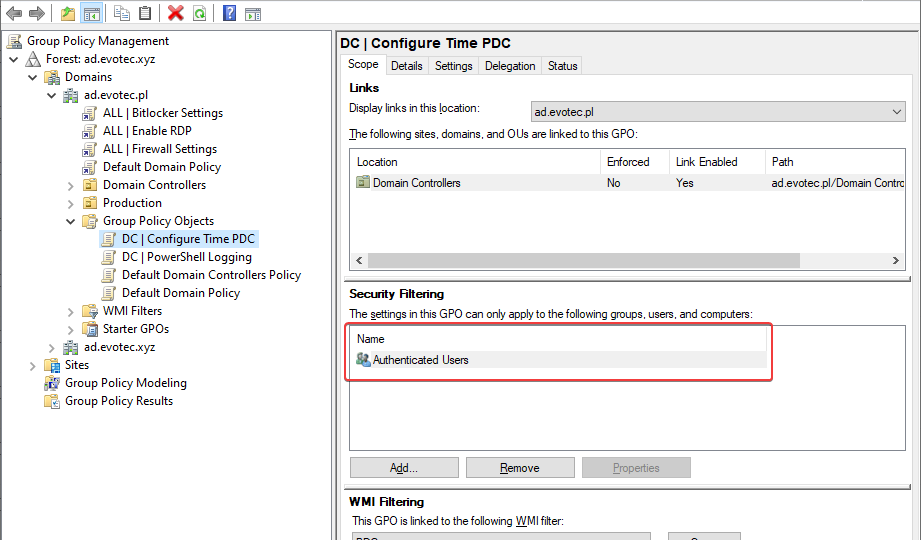
I’ve been in IT for a longer time now. I’ve made my fair share of mistakes and misconfigurations. One of those misconfigurations was removing Authenticated Users from Security filtering in Group Policy Objects. While it worked fine at some point Microsoft rolled out a Hotfix MS16-07 on June 14th 2016.
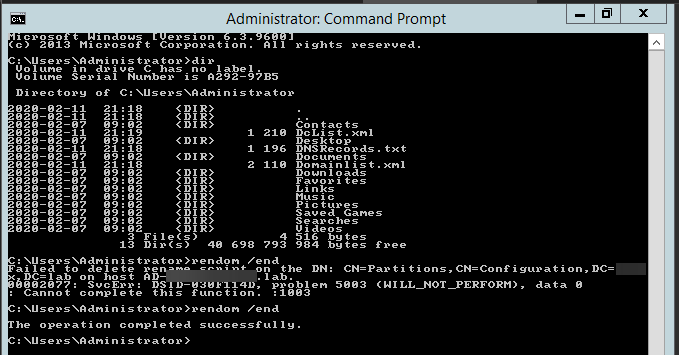
Recently I was testing renaming the NETBIOS name of an Active Directory domain. While this process is fairly easy, there are a few gotcha’s, and before one would like to rename their domain or NETBIOS name, serious testing is required to be sure everything works after rename. In the end, if something goes wrong, the rollback will not be a walk in a park. It will hurt, and it will eat your time. So there was I going thru the usual steps.
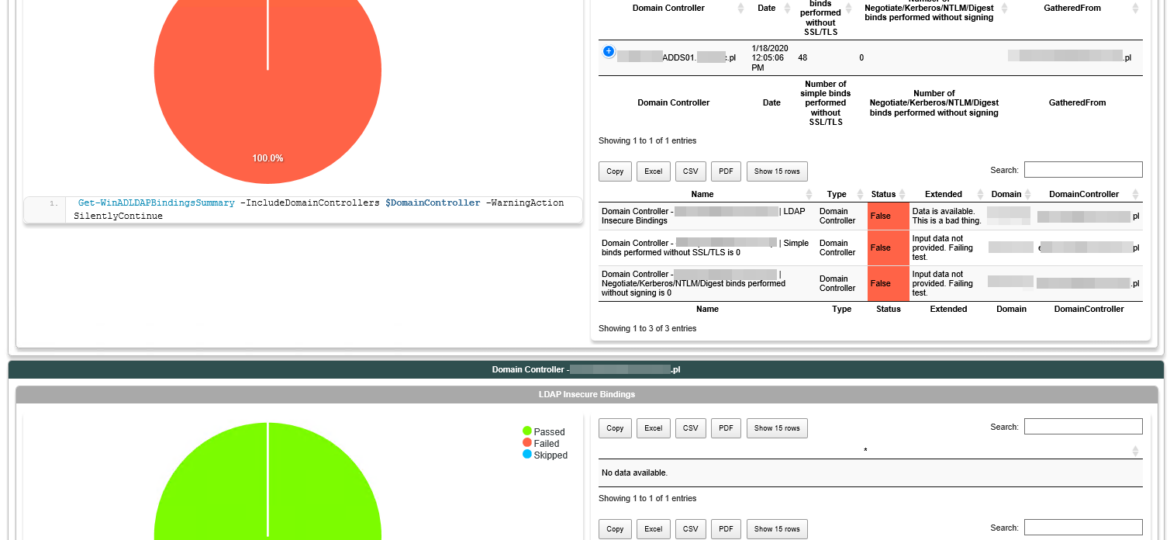
In March 2020, Microsoft will release its monthly updates. With those updates, Microsoft will disable insecure LDAP Bindings, which is going to break a lot of your systems (hopefully not). But this was already communicated, and you know all about it, right? If not, you should read those two articles that can help you with understanding what is happening and when.
It’s year 2020 and 365 days passed since my last year blog post about PowerShell modules I worked on in 2018. I thought it would be a good occasion to review what happened and how things changed during that time. When I wrote the last blog post in the first days of 2019, my PowerShell modules were downloaded just a bit over 15000 times. Fast Forward today, and the counter is at 280000 times spread over 40 modules. Of course, not all those modules are equal. In 2019 I created multiple new PowerShell modules, but some modules were archived, while others were migrated back to their „parents”. Just to see how my community road was going in the last years I decided to check some statistics.