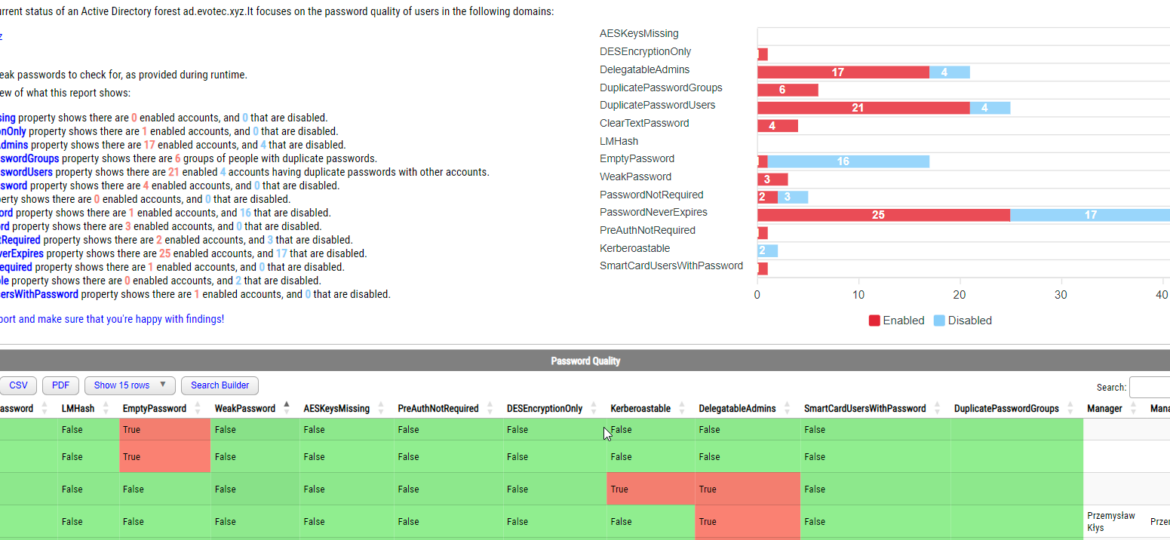
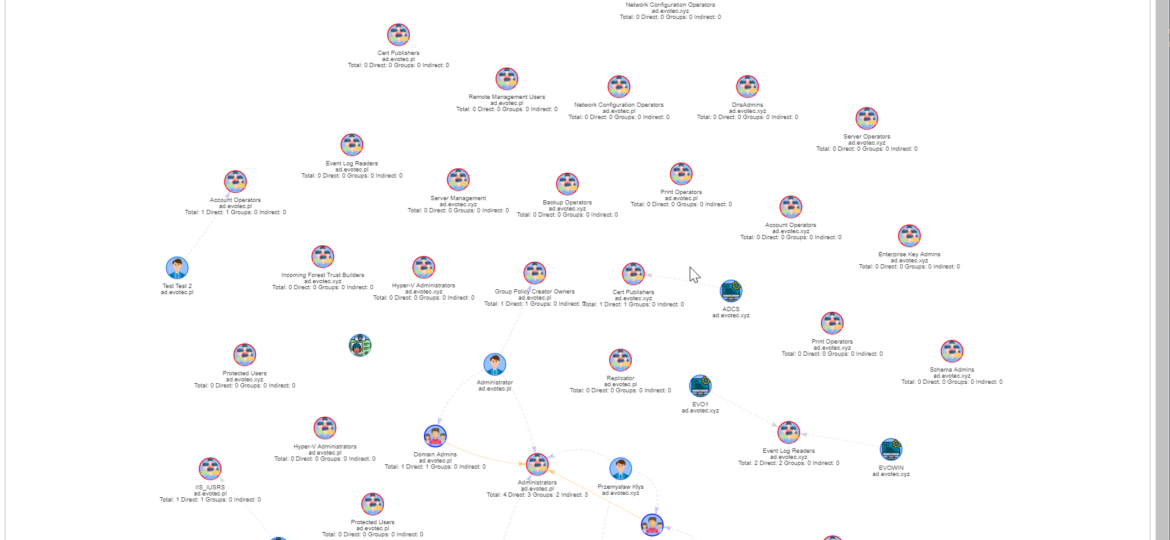
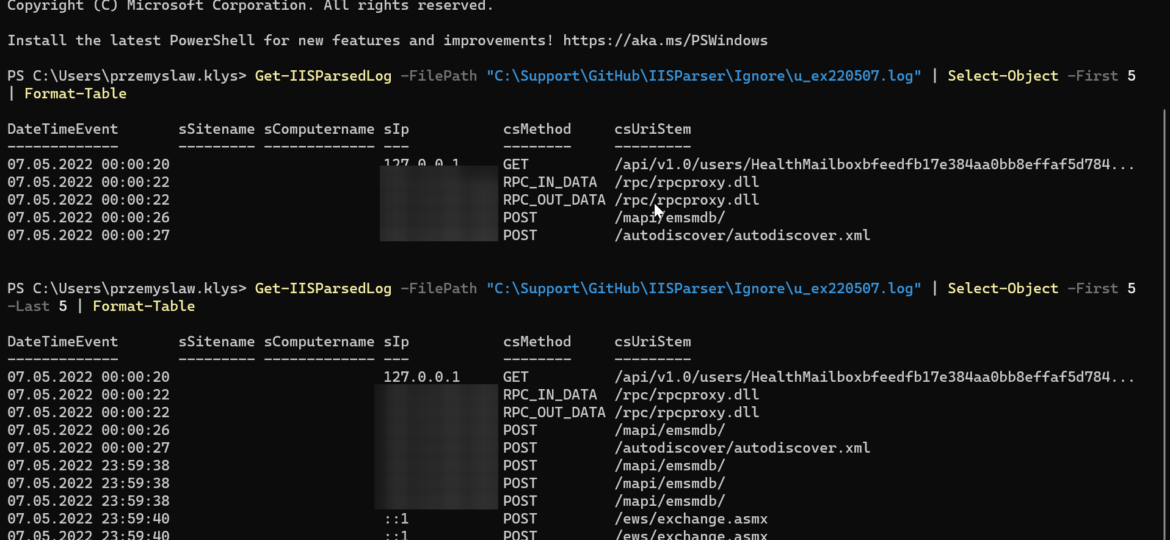
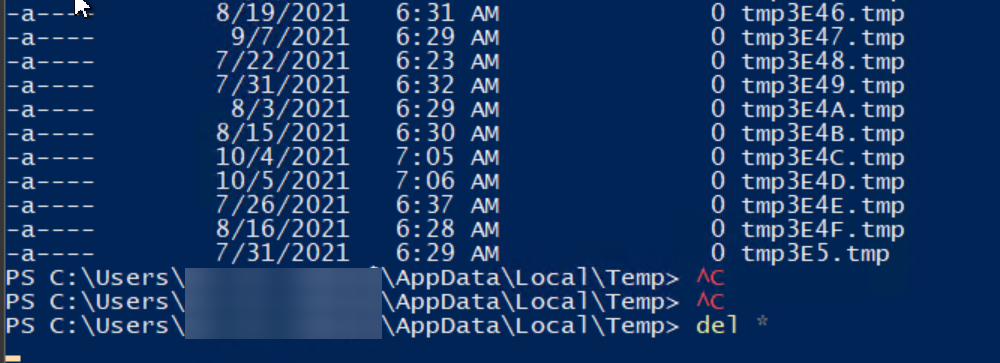
PasswordSolution uses the DSInternals PowerShell module to gather Active Directory hashes and then combines that data into a prettified report. If you have ever used DSInternals, you know that while very powerful, it comes with raw data that is hard to process and requires some skills to get it into a state that can be shown to management or security.
Windows
I work a lot with Active Directory-related tasks. One of the tasks is to know the group membership of critical Active Directory Groups such as Domain Admins, Enterprise Admins, Schema Admins, Event Log Readers, and a few others that are a bit less known. As I did it, I got bored of typing the group names repeatedly and decided that enough was enough and there must be an easier way for me to do that.
I’ve created a cross-platform (Windows, Linux, macOS) Word library based on Open XML SDK that heavily simplifies creating and modifying Word documents. Open XML SDK, while excellent, requires you to do a lot of work to make even simple documents. For example, if you want to use Table styles, you need first to define those styles, put them in a specific place, and assign them to a table. The same goes for lists, images, hyperlinks, bookmarks, and many other Microsoft Word types. Creating sections, managing headers, and footers – all that is possible using Open XML SDK, but it’s far from easy. At least for a noob like me. You have to know the order to put them into the document; you must know the places and track IDs to all the elements. And trust me – it’s not fun.
Today I was reading Twitter, as I am pretty addicted to technology news when Adam Bacon mentioned that he’s surprised that no one has rebuilt IIS Parser as pure PowerShell. While this is not entirely true, and some modules can do some parsing, I decided to try my luck. While doing it from scratch in PowerShell is possible, I opted to use an external C# library that does all the heavy lifting and is optimized for speed.
Today’s story is about me making assumptions on how things work based on the method’s name. As the blog post says, I want to focus on two similar methods – GetTempFileName() and GetRandomFileName(), when using PowerShell. Still, since those methods are .NET based, it applies to a whole range of other languages – C#, F#, VisualBasic, and all others that I’ve never used.
If you ever encounter an error while trying to create a new domain within a forest saying, „The replication operation encountered a database error,” it makes you sweat a bit. Your brain tells you it will be a nightmare to fix, do I have proper backups to make it happen, and the question „why now” shows up.
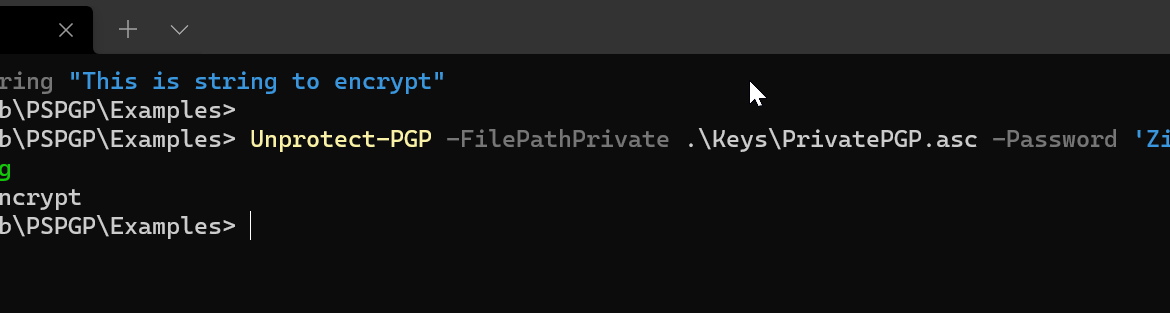
Some time ago, I decided that having an easy-to-use PGP PowerShell module is a way to kill my boredom. Four months have passed, and I decided to share it with the world, as it may be helpful to some of you. Today I would like to introduce you to PSPGP – PowerShell module that provides PGP functionality in PowerShell.
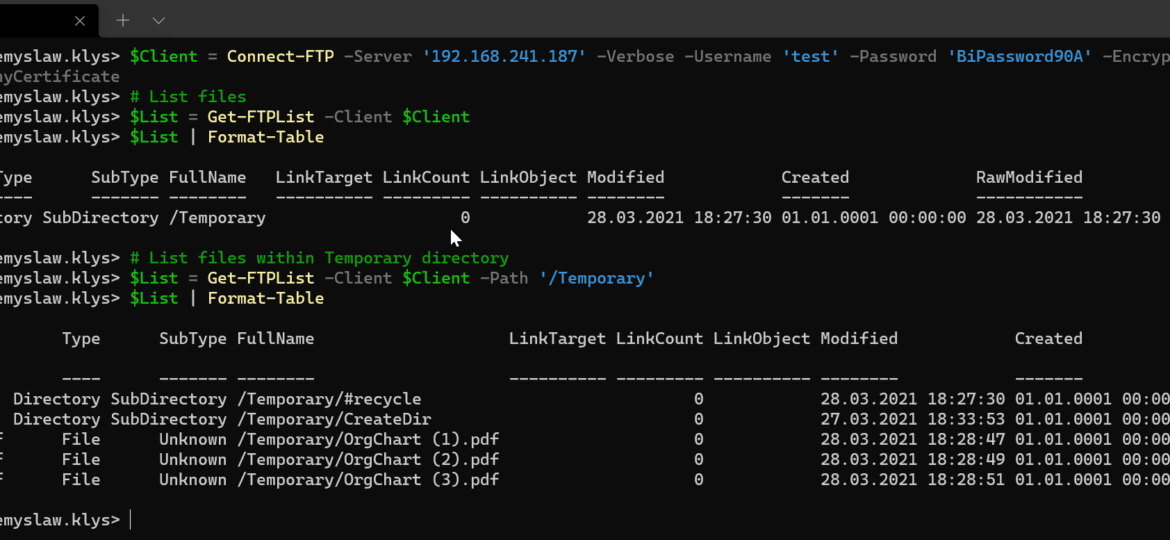
FTPS and SFTP are two ways to send and receive files from remote sources. While the name suggests both do the same thing, those are different protocols, in the end, having the same goal. A few weeks back, I had to make sure I can reliably download files from FTPS server using PowerShell, and since I couldn’t find anything straightforward to use, I decided to write my own. Transfertto is a new PowerShell module that supports both FTPS and SFTP protocols. Its goal is to be the only module that you need to transfer files to and from FTP/SFTP servers.
I like OneDrive. It allows me to keep my data secure and always synchronized. If things go wrong, I can always get it back. I use it for almost everything. Even for my PowerShell projects, which are committed to GitHub, so in theory, I shouldn’t need that. But every once in a while, I make some stupid mistake and delete a file that has yet not been committed to GitHub, and that’s where the OneDrive comes in handy. Quick restore, and we’re back. Unfortunately, sometimes things aren’t as I would expect them to work. For example, let’s have a look at this nice list of markdown files that are documentation for my module called GPOZaurr.
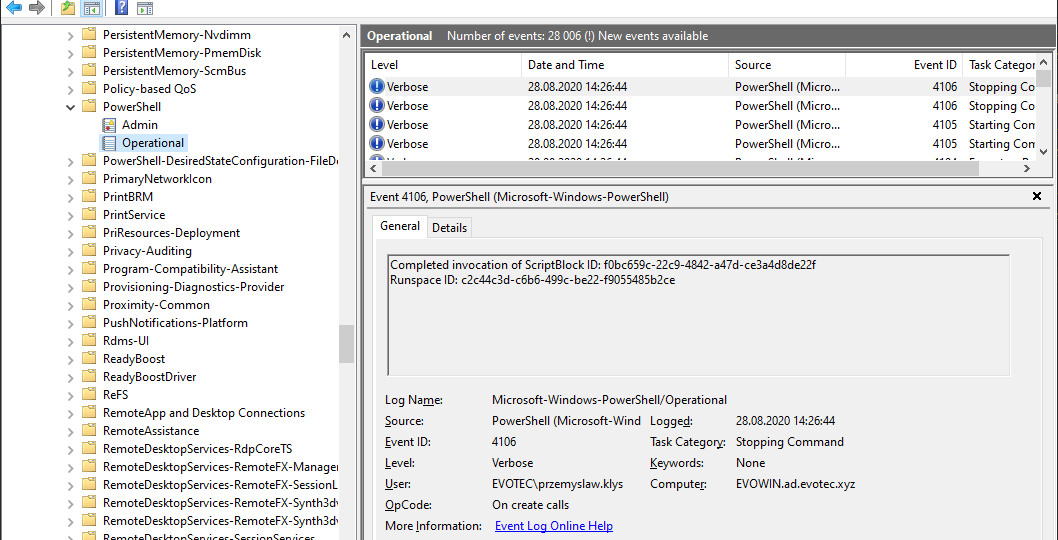
A few days ago, I was asked to take a look at PowerShell Malware. While I don’t know much about malware, my curiosity didn’t let me skip on this occasion, and I was handed over WindowsPowerShell.evtx file. Ok, that’s not what I expected! I wanted PowerShell .ps1 files that I can read and assess? Well, you play with the cards you were dealt with. What I was handed over was PowerShell Event Log. PowerShell writes whatever you execute, and it thinks it is risky, to Windows PowerShell Operation Event Log.