I had this little issue today when I tried to schedule the Microsoft Graph script to run as a service account on a certificate. To my surprise, even tho I had all permissions required, I was getting this error message: Connect-MgGraph: Keyset does not exist. Something that didn’t show up for my user.
powershell
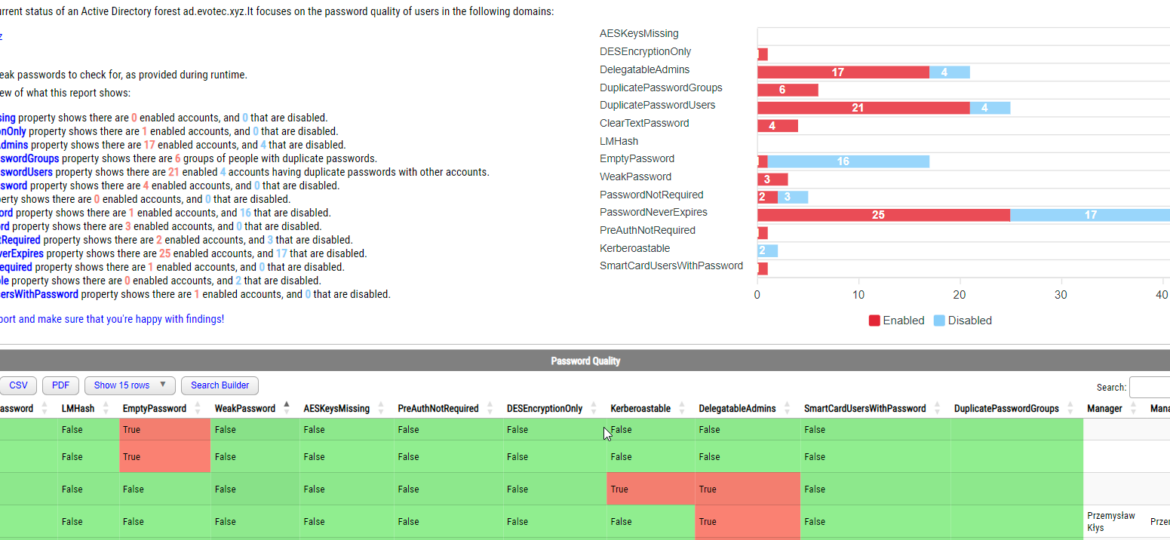
PasswordSolution uses the DSInternals PowerShell module to gather Active Directory hashes and then combines that data into a prettified report. If you have ever used DSInternals, you know that while very powerful, it comes with raw data that is hard to process and requires some skills to get it into a state that can be shown to management or security.
I am a pretty big fan of Ubiquiti and their Unifi products line. Whether it’s network equipment or their camera systems, Unifi Protect, I have it all, and I’m pretty happy with how it works. However, over the last two years, some of their stocks in the store were very hard to find. For example, I’ve searched for Unifi Protect G4 Doorbell Pro for over six months. I’ve tried local shops all around Europe, even in the Ubiquiti Europe store, to never found any of them.
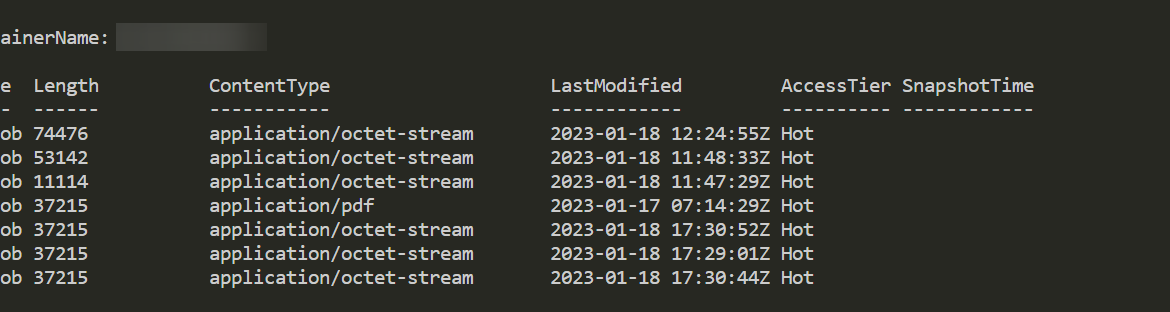
They say there is a first time for everything. For me, it’s how to download and upload files to Azure Blog Storage using Connection String. Recently I was given Connection String, Container name and had to download some files from Azur Blog Storage. After some research and trying Connect-AzAccount, I found that the proper way to go is thru New-AzStorageContext.
When I created ImagePlayground, I thought about how to show its usefulness to the general community. On how to deliver what PowerShell can do. Then I saw on some forum people asking BGInfo to expand and allow running PowerShell scripts so that the data on the BGInfo Wallpaper can be gathered from PowerShell rather than VBS. I thought this was a great idea to create BGInfo using PowerShell without the necessity of using BGInfo at all.
ImagePlayground is a PowerShell module that works in PowerShell 5.1 and PowerShell 7+. It works partially on Linux and should work on macOS, except for charts. That means it’s partially cross-platform, but the end goal is to make it work fully on all platforms. So what can this module do?
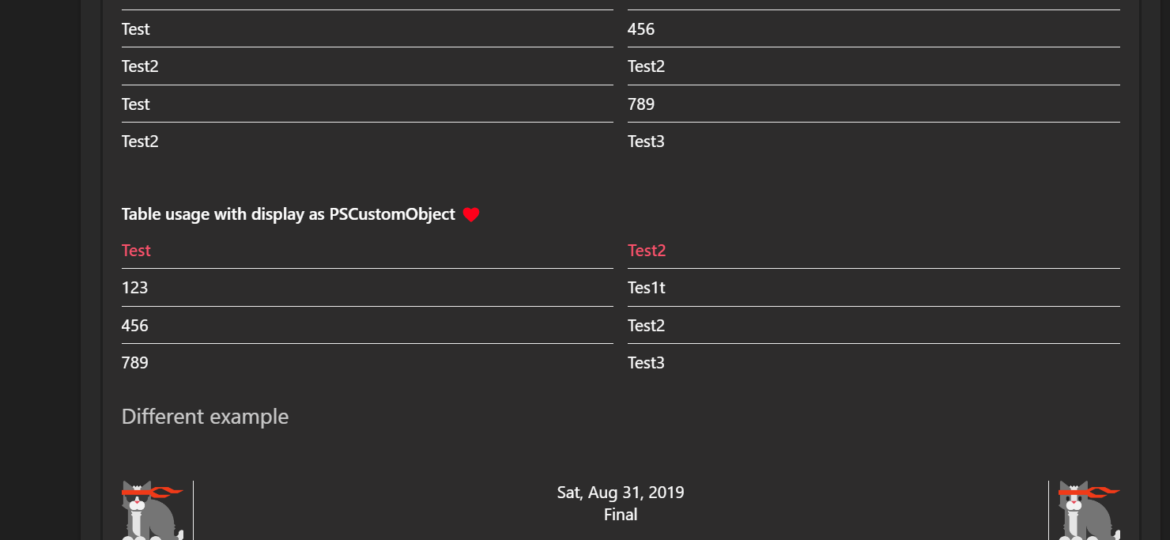
PSTeams is a PowerShell module that helps simplify sending notifications to Microsoft Teams via Incoming webhooks. It’s easy to use and doesn’t require playing with JSON. Since version 2.0, it started to support Adaptive Cards; in version 2.1, I’ve added the ability to mention people. Today I’m introducing an easy way to send data as a table and a quick way to add a line break.
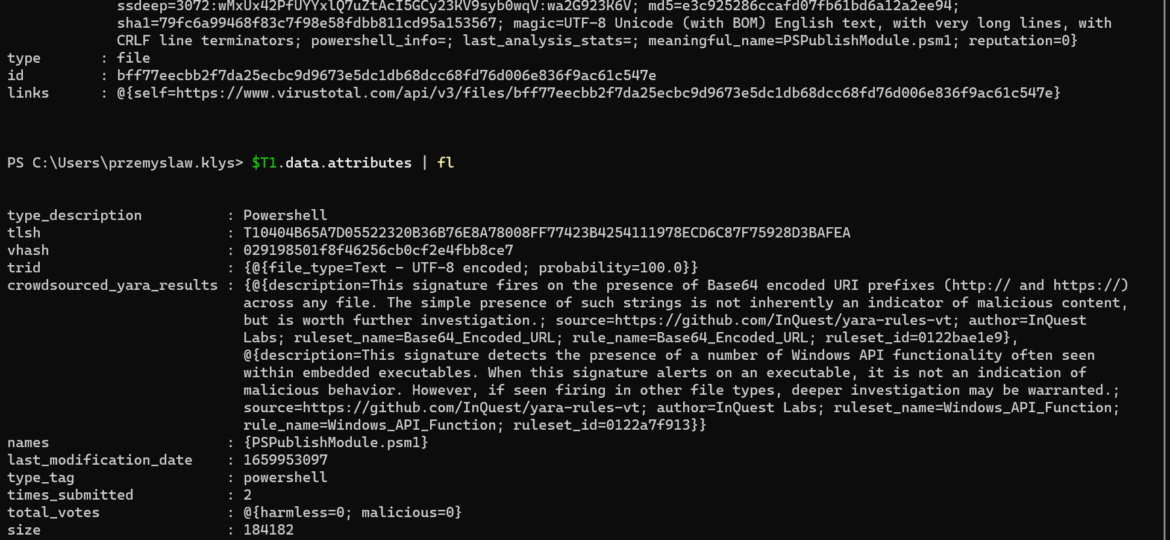
Virus Total is an excellent service. It’s a single place where hundreds of antivirus engines can verify if the file, URL, domain name, or IP Address is trusted or not. Of course, it’s not a silver bullet, but it brings tremendous value, and I often verify files I download before executing. Since I release a lot of new or updated PowerShell modules on a weekly/monthly basis, I thought it would be great to send newly released versions straight to Virus Total so I can have them checked before anyone executes them. I also hope to prevent false positives from some antivirus vendors that may tag my modules as malware because they haven’t seen the DLL or PowerShell module in this form before. I’ve seen it happen to DBATools, so why not try and push my modules before users even use them?
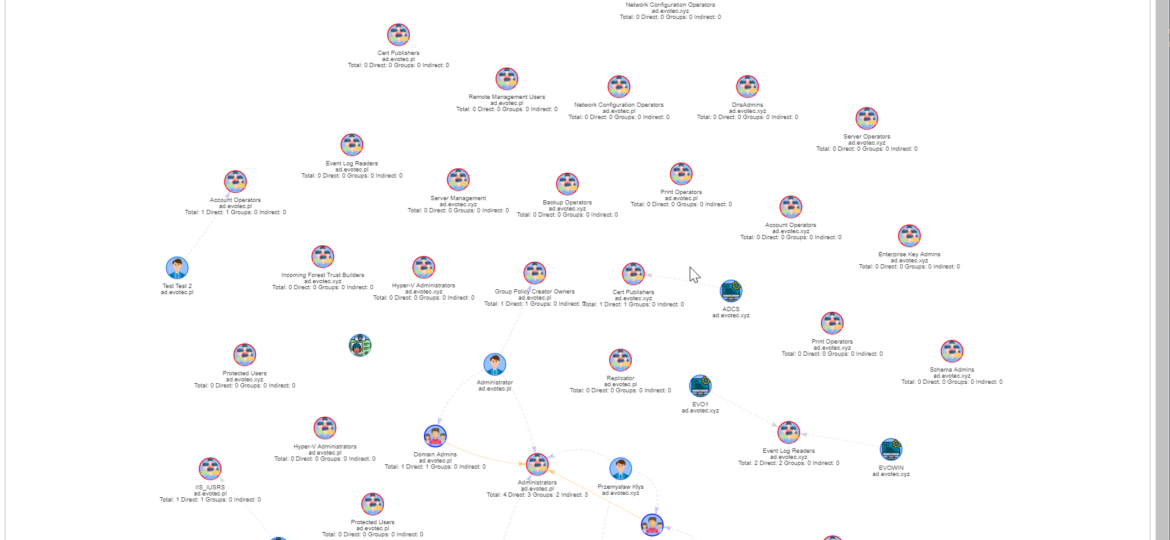
I work a lot with Active Directory-related tasks. One of the tasks is to know the group membership of critical Active Directory Groups such as Domain Admins, Enterprise Admins, Schema Admins, Event Log Readers, and a few others that are a bit less known. As I did it, I got bored of typing the group names repeatedly and decided that enough was enough and there must be an easier way for me to do that.