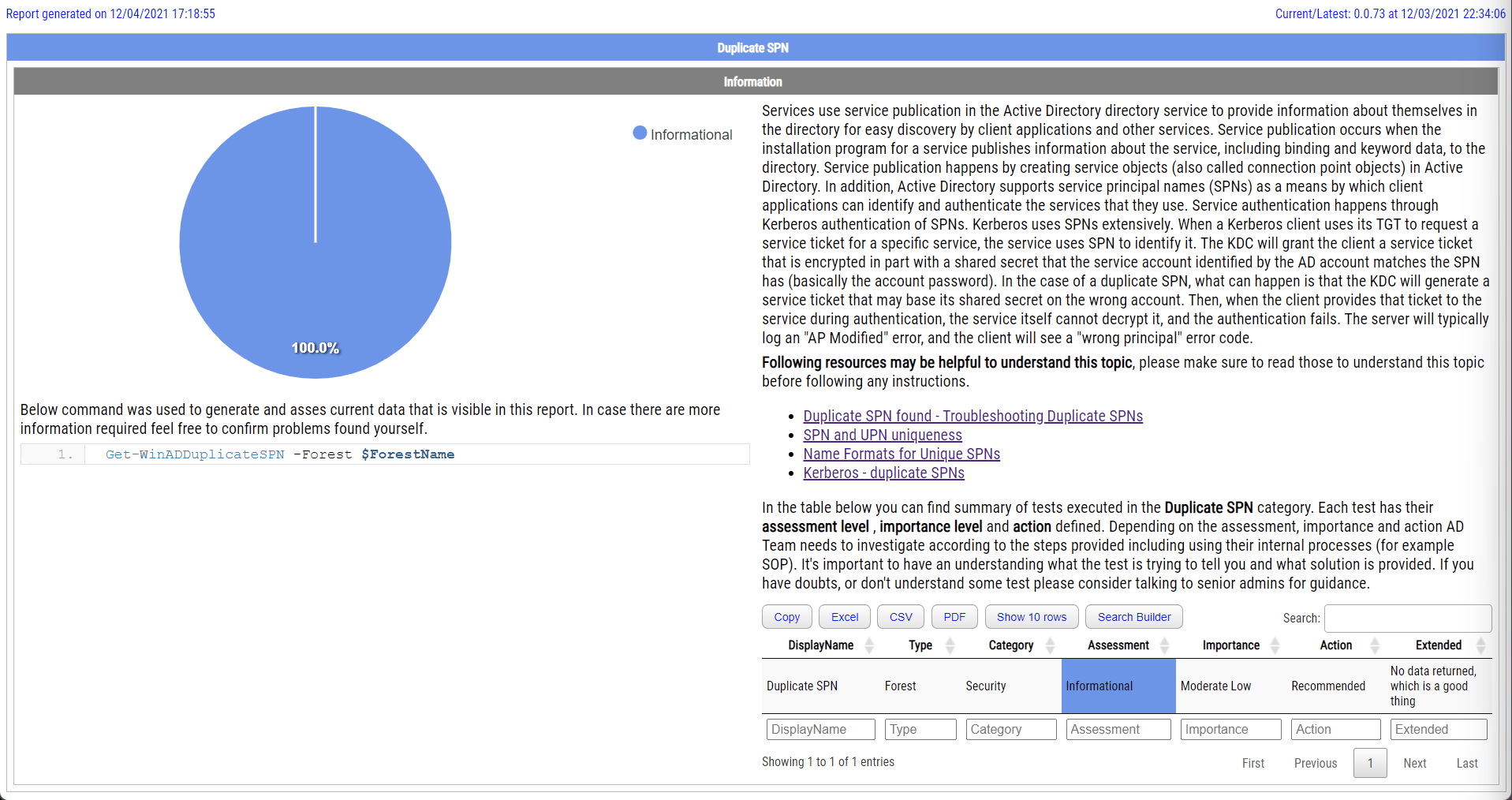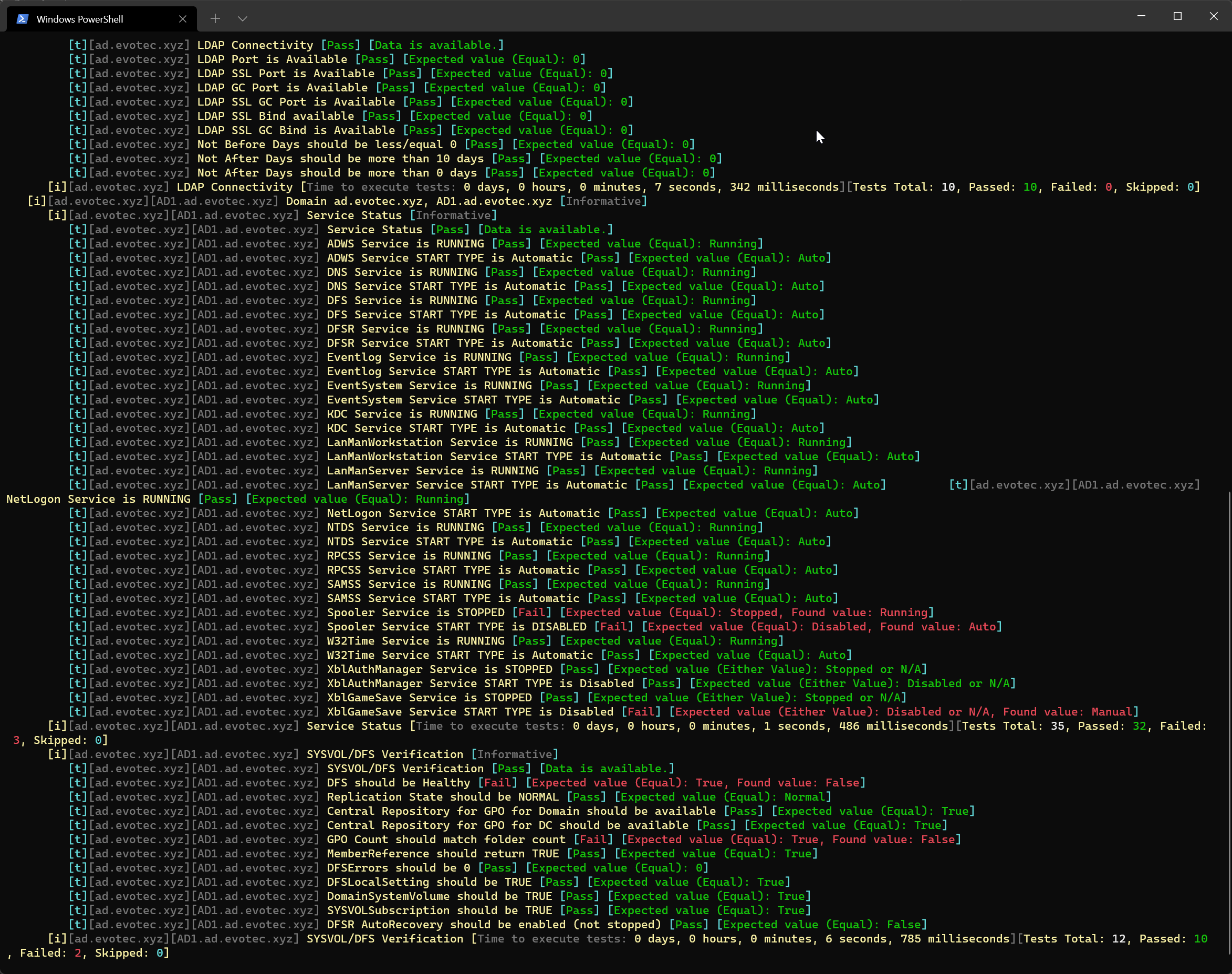
Duplicate SPNs aren't very common but can happen in any Active Directory as there's no built-in way that tracks and prevent duplicate SPN's. One has to either know all SPN's in the environment, track them or check each time whether it already exists or not. Things get more complicated with larger Active Directory environments as people change, new apps are added, old apps are forgotten, but SPNs prevail.
💡 Duplicate SPN
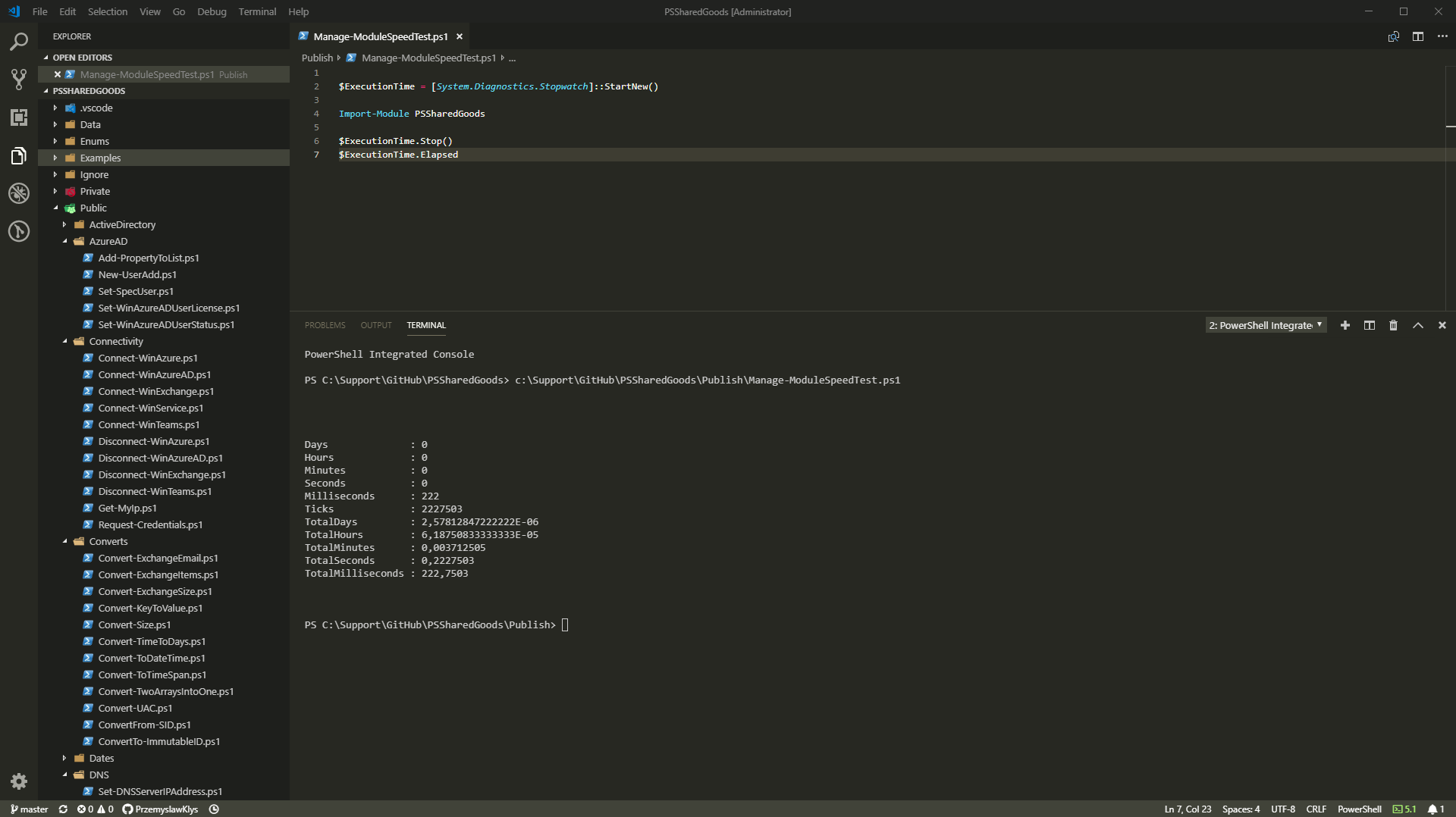
As I invest more time in proper AD Compliance & Hardening tools for my Active Directory, I've added yet another test to Testimo.
The report above, like any other report from over 80 reports from Testimo can be generated with a single line of code.
Invoke-Testimo -Sources ForestDuplicateSPN
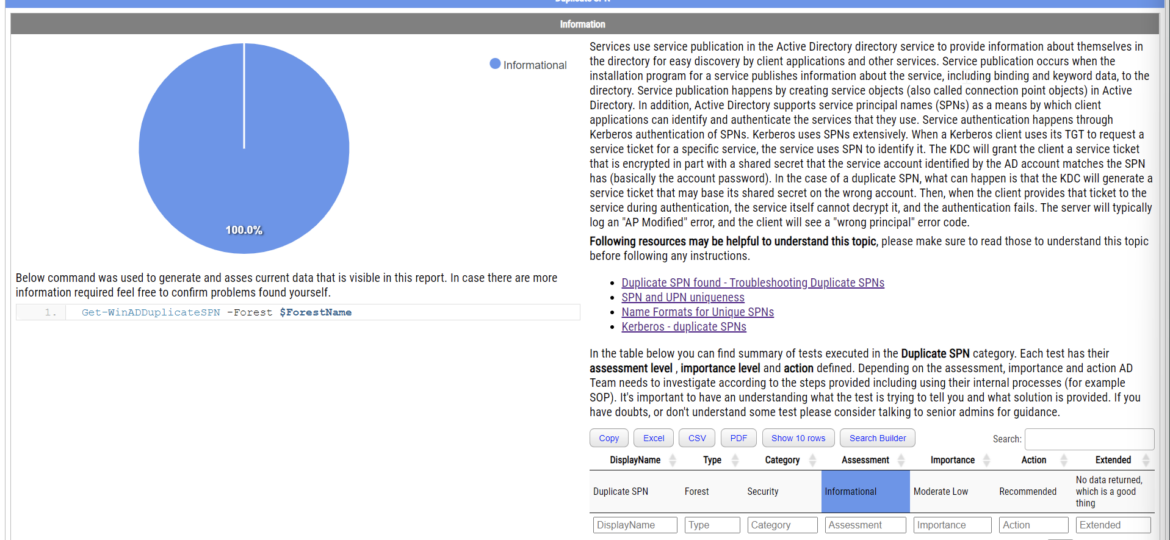
Of course, the report above shows there are no duplicate SPNs, but I have tiny AD and keep things tidy 🙂 But your production environment may not be as clean as you think it is.
💡 Duplicate SPN in Testimo/ADEssentials
Testimo is a PowerShell module that doesn't have Active Directory code. It's a bit more like a wrapper around multiple other modules. It integrates GPOZaurr, ADEssentials, PSSharedGoods, PSWriteHTML or PSEventViewer. All written by me, all are doing their part. ADEssentials contains a command used by Testimo to provide a graphical representation of it. By using Get-WinADDuplicateSPN without any parameters, you can quickly find duplicate SPN's.
Get-WinADDuplicateSPN | ft
You can also use All switch if you would like to see all SPN entries instead of just duplicates.
Get-WinADDuplicateSPN -All | ft
In Testimo, I wrap around it and assess how good or bad the given data is. The assessment, of course, is based on my judgment, and you can disagree. It's more of a guidance than anything else, so make sure you diagnose why this is rather than going through and fixing everything it tells you to improve. In Testimo, I also try to add descriptions and links that you may find helpful in figuring whether the test makes sense to your environment.
💡 Summary
If you want to find out more on ADEssentials, Testimo, or GPOZaurr I encourage you to search my blog for those terms and you'll find a description of how to utilize those to your advantage. Those modules provide an easy way for AD Compliance & Hardening to tell you what's wrong and how you can fix it.
- 🌐 The code is published on GitHub
- 🌐 Issues should be reported on GitHub
- 🌐 Code is published as a module on PowerShellGallery
The module is signed with a certificate, like any new modules that I create or update.
Install-Module Testimo -Force
GO Ahead! Have fun! Make sure to report any issues, or if you feel like something would require covering more ground, let me know.