Active Directory Trusts are useful to connect one or more domains. But as useful those are, they can be very dangerous. Also, keeping trusts working and in good shape should be a top priority for Active Directory Admins. While there is a couple of command in the Active Directory module Get-ADTrust, I thought I would try and write my own that checks a few more things. I want to thank Chris Dent for his input on the part of this command. His binary skills amaze me!
💡 Get-WinADTrust – cmdlet to get Windows Active Directory Trusts Recursively
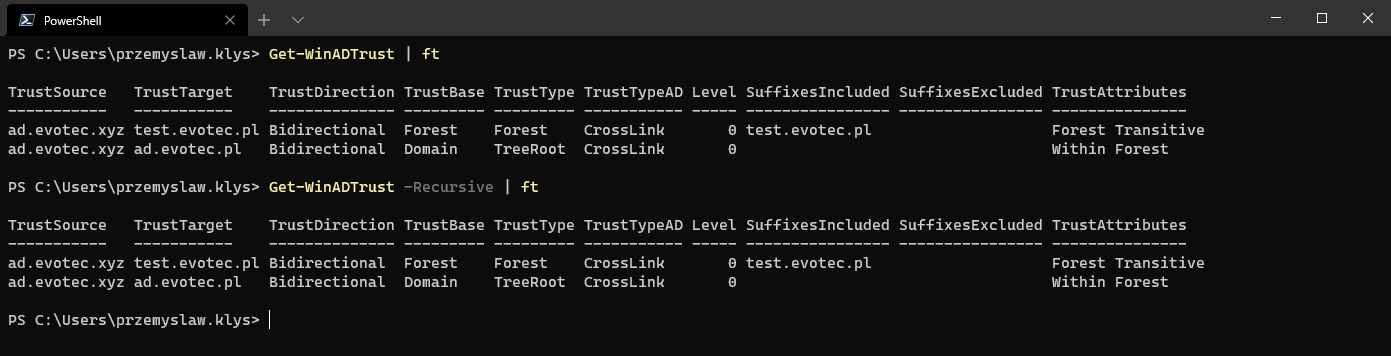
Get-WinADTrust | ft Get-WinADTrust -Recursive | ft
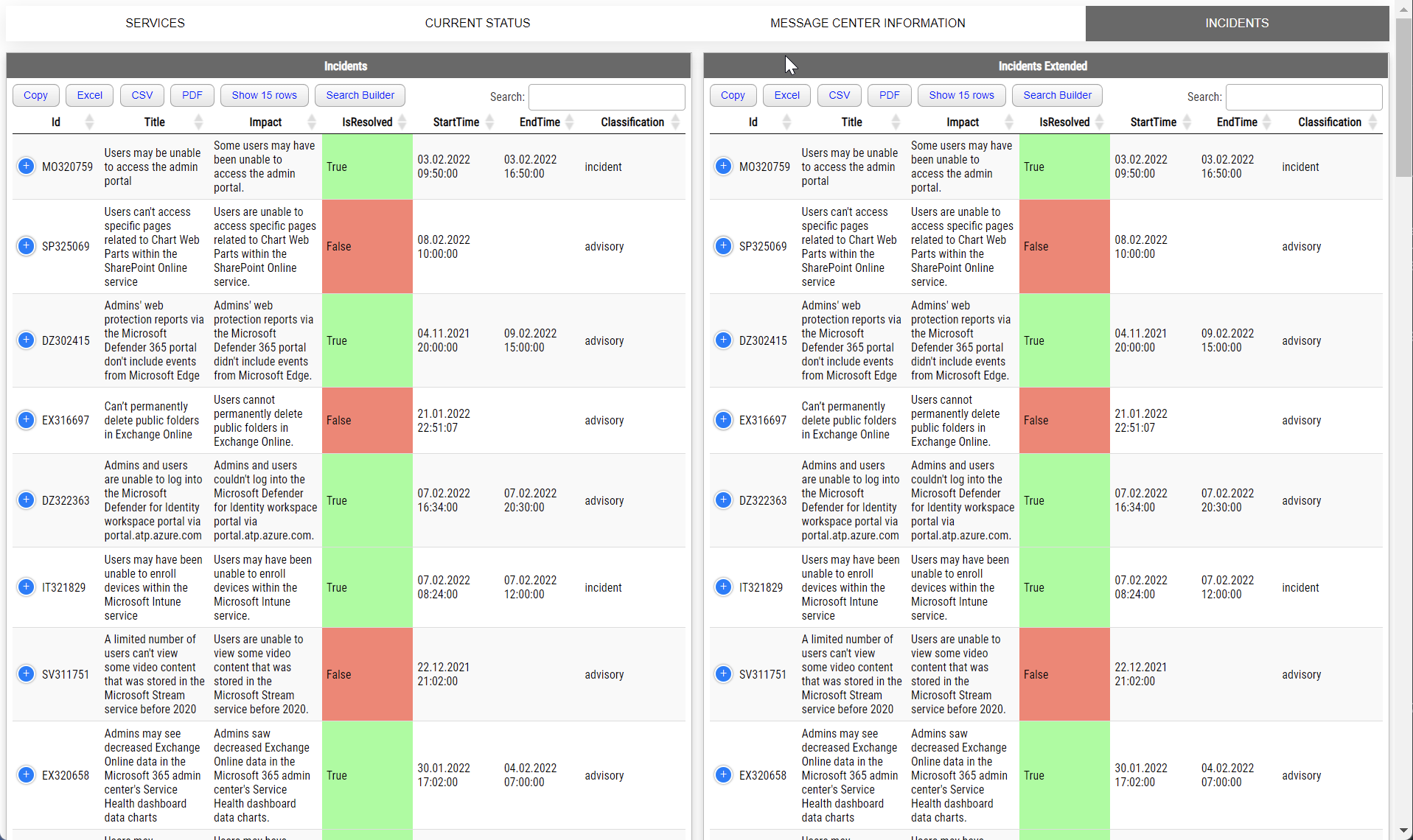
The first command is called Get-WinADTrust. Aside from providing detailed information, it also contains a Recursive switch, which tells the command to try and follow the trusts as much as it can. If we check what, each trust in Get-WinADTrust contains, we're going to get a nice list of properties.
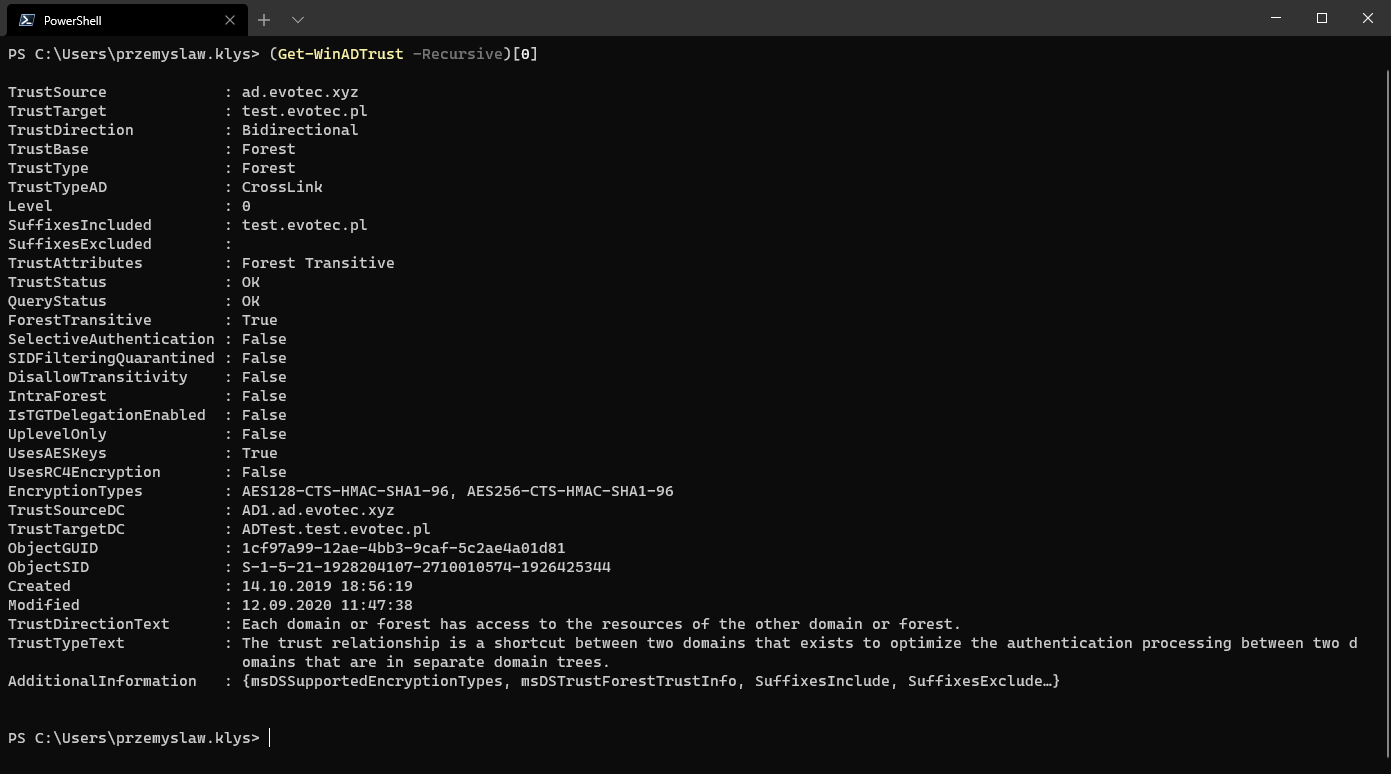
(Get-WinADTrust -Recursive)[0]
You should notice two properties TrustStatus and QueryStatus. If you're a Domain Admin, what the TrustStatus will do is verify the tunnel using WMI and report if it's working correctly or not. Of course, if you're not Domain Admin, this command won't help as you won't be able to query WMI on Domain Controller. This is where QueryStatus comes in. For each trust, the command queries the Administrator group within that domain. If it can resolve it, the status is OK. If it can't, it's not. This allows you to verify trusts are working or not based on AD Query even as a standard user in your domain. Of course, it's possible the trust is working, but the way it's configured prevents you from querying users/groups on the other end of the trust. That's not all.
Get-WinADTrust has nested properties inside AdditionalInformation property. It includes information like Suffixes used for the trust and their state. This is where I'm using Christ Dent skills to provide the status of a suffix, whether it's enabled, disabled, or in conflict.
You can also see details of the group that was queried while checking trusts. Of course all other stuff such as TGT Delegation status and few others are directly exposed for easy filtering.
💡 Show-WinADTrust – cmdlet to show Windows Active Directory Trusts Recursively
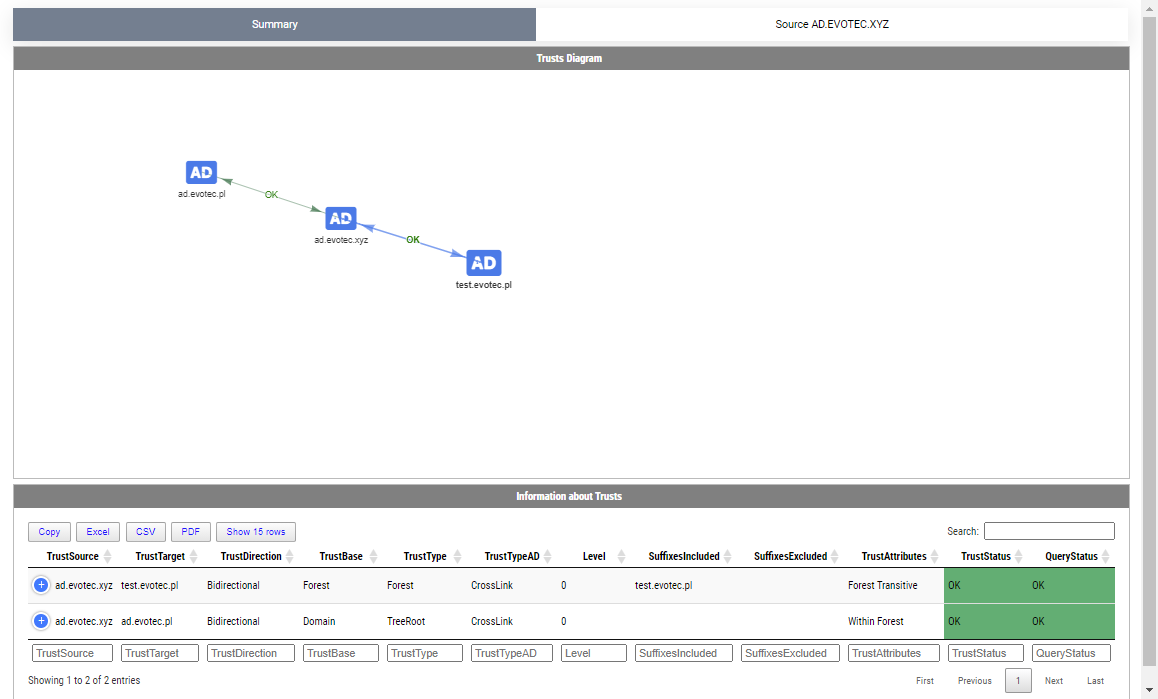
Get-WinADTrust is a bit more advanced copy of Get-ADTrust. Show-WinADTrust is a visual representation of it. The usage is mostly the same
Show-WinADTrust -Online -Verbose -Recursive
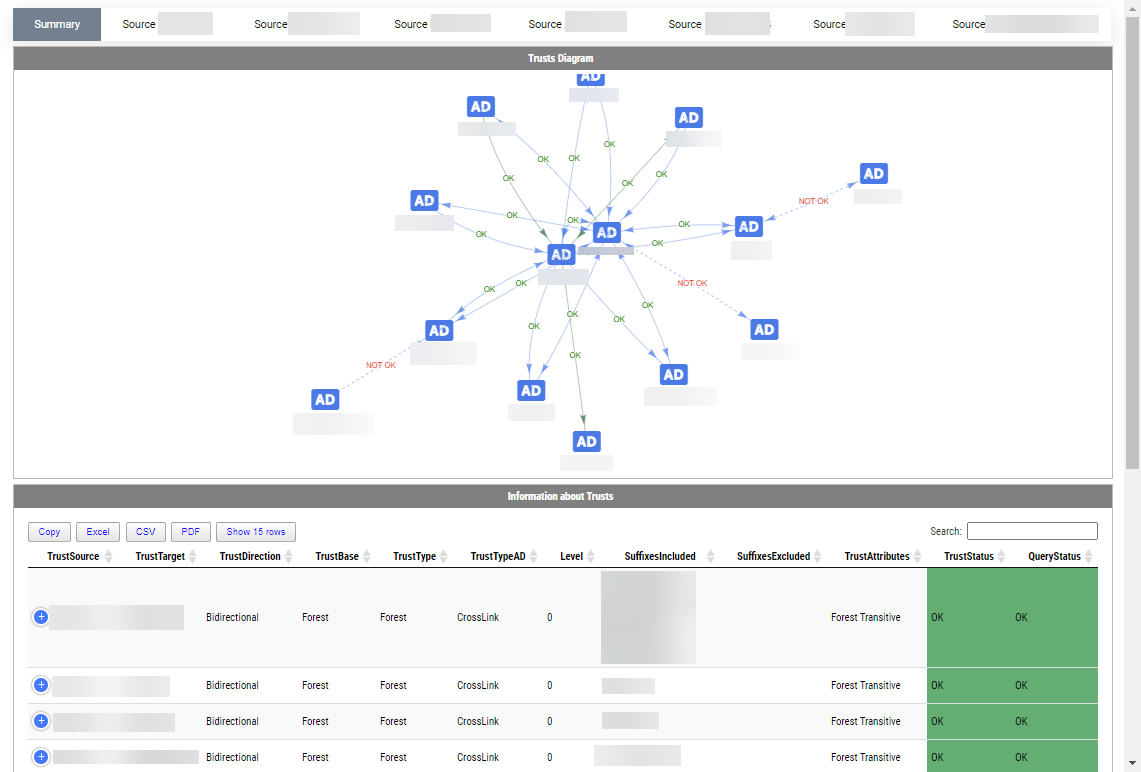
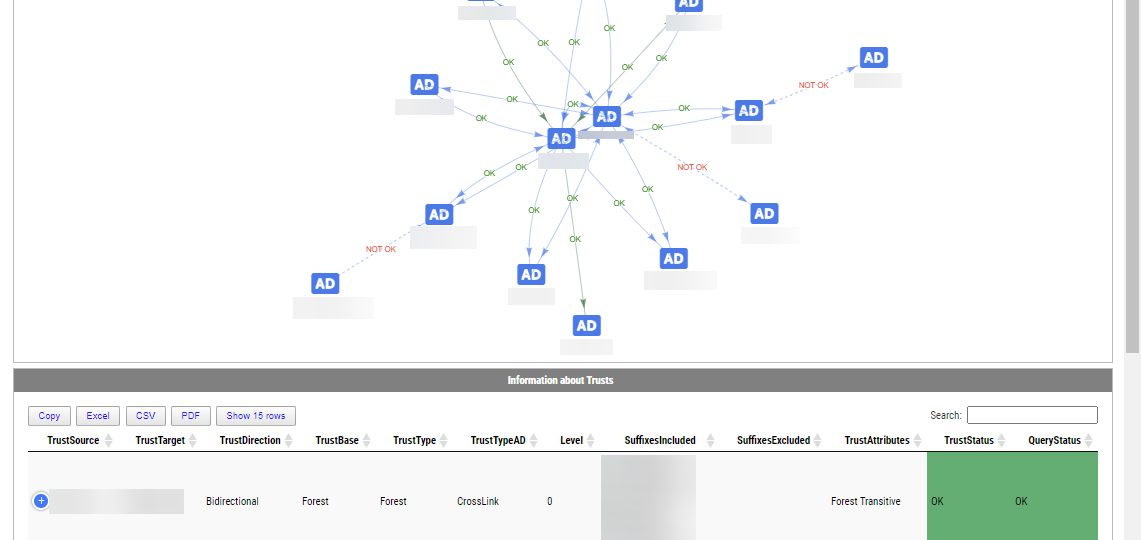
While the above may not be a very impressive trust summary, it scales with the number of trusts you have. You get the Summary tab, which gives you a diagram on how all trusts are connected and whether or not they work. I've added some colors, but haven't spent much time adjusting them (may do so in the future). At the bottom of the diagram, you get a list of your trusts. Then for each source trust, you get another tab under which for each source you have nested tabs with target trusts, with some more details about trusts that are easily visible. Again, I've added some colors here, making them easier to spot.
As always, with diagrams generated via PSWriteHTML, you can right-click on a diagram and save it to the image. As always, with PSWriteHTML tables, you can also save things to excel without much effort on your side. To show you how it would look like with more trusts, here's a summary view
While I have made some of my own color choices for the primary table, I also added the ability to do that on your own.
💡 Show-WinADTrust – conditional formatting to suite your needs
Adding conditional formatting in tables is directly supported by PSWriteHTML, so all I needed to do is expose the ability to use PSWriteHTML New-HTMLTable options and provide them to you. All that means that whatever is supported by New-HTMLTable nested commands can be utilized in Show-WinADTrust.
Show-WinADTrust -Online -FilePath $PSScriptRoot\Reports\TrustsWithColors.html -Verbose {
TableHeader -Names 'TrustBase', 'TrustType', 'TrustTypeAD' -Color Blue -Title 'Types'
TableCondition -Name 'TrustDirection' -BackgroundColor red -Color white -Value 'Bidirectional' -Operator eq -ComparisonType string
TableCondition -Name 'Level' -BackgroundColor blue -Color white -Value 0 -Operator eq -ComparisonType number
}
With three lines of code using TableHeader, TableCondition cmdlets, I was able to make conditional formatting in the table. And if you dislike the default colors I did to the table, you can always remove it with the DisableBuiltinConditions switch.
If you have seen Visually display Active Directory Nested Group Membership using PowerShell the same logic applies there. If you're using that command you can apply any conditional formatting using the newest version of ADEssentials.
💡 Installing ADEssentials
Those cmdlets are part of the ADEssentials module that I've been enhancing for some time now. All you need to do, to install it is:
Install-Module ADEssentials
While most of the commands in the ADEssentials module require RSAT (ActiveDirectory/GroupPolicy) to be present to work, actually commands described in this article don't. Cmdlets itself are ADSI based, so they don't need RSAT to work, but other cmdlets from ADEssentials do.
When you install-module, it will also install PSWriteHTML and PSEventViewer. The first one is required for displaying output in HTML (tables/diagrams). The other one is a wrapper around Get-WinEvent and is used by some of the commands available within ADEssentials. Install-Module will do all that installation for you without doing anything except for the RSAT requirement, but if you're AD Admin, you should already have those up and ready to use. If you don't have admin rights on your workstation it's still possible to use this module.
Install-Module ADEssentials -Scope CurrentUser
As those cmdlets described above are read-only, they don't require any rights in AD. I've been digesting my production environments using my standard ID. For sources, reporting issues, or feature requests, as always, visit GitHub. All my projects are hosted on it, and it's preferred method of providing support.