User Account Control (UAC) is a feature in Windows that can help you stay in control of your computer by informing you when a program makes a change that requires administrator-level permission. UAC works by adjusting the permission level of your user account. If you're doing tasks that can be done as a standard user, such as reading e‑mail, listening to music, or creating documents, you have the permissions of a standard user—even if you're logged on as an administrator. However for Windows Server where most of the tasks are done by Administrators by default it's often getting disabled by Administrators.
❓ Problem Description
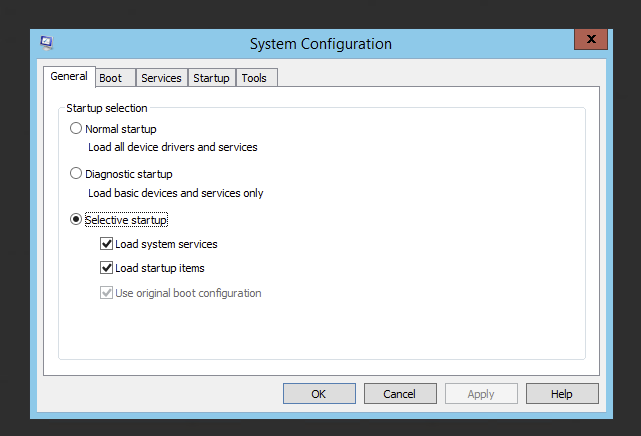
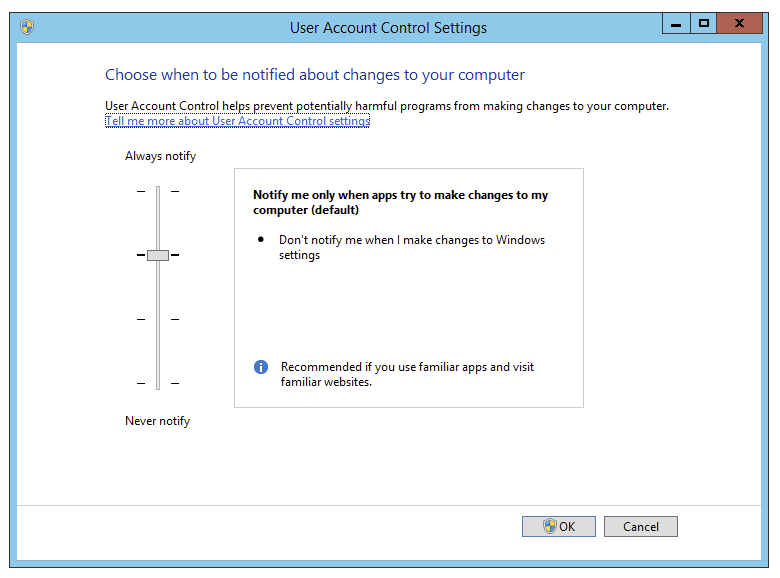
Most administrators will disable UAC (User Access Control) using standard approach as it was standard procedure since Windows Vista, continued thru Windows 7 and other client systems. To do that you just had to:
Press START
Type in msconfig to start System Configuration tool
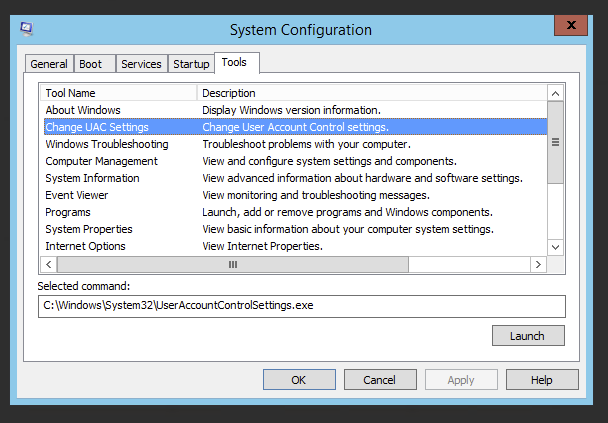
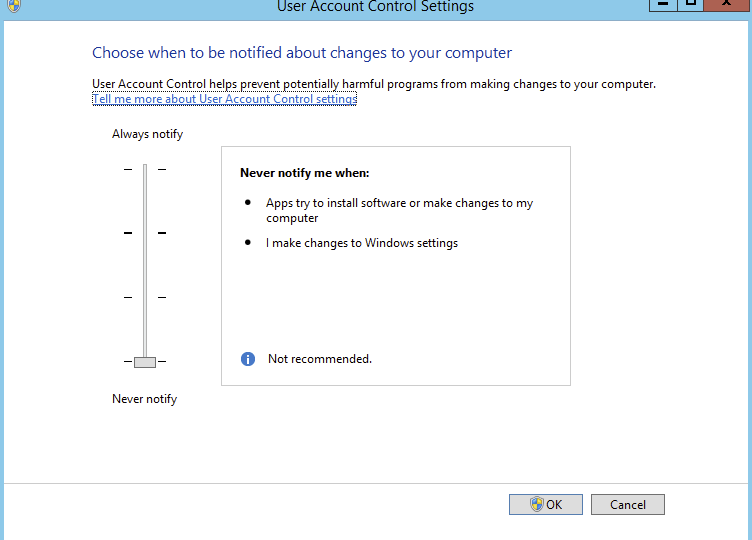
Switch to Tools Tab, and choose Change UAC Settings
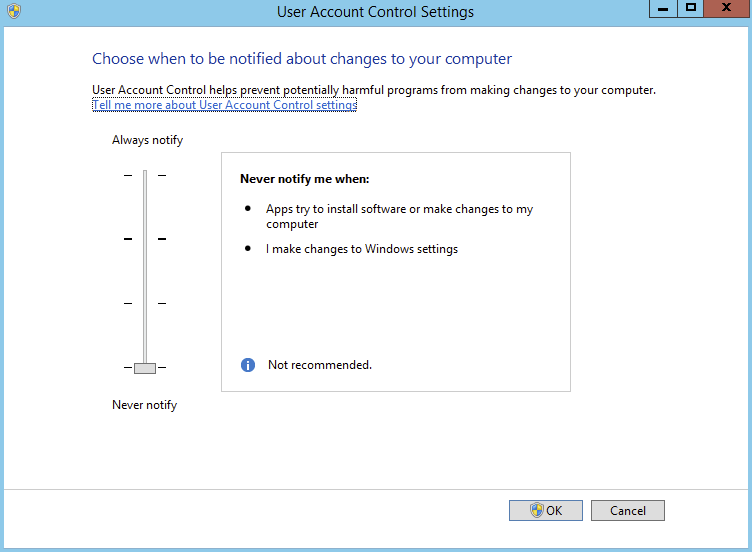
And finally modify settings by choosing Never Notify
While this modification has worked fairly well in Windows client systems (I have not seen the drawbacks of this change), this change in Windows server systems doesn't always go well. It changes some behaviour such as:
CMD prompt gets started as Administrator
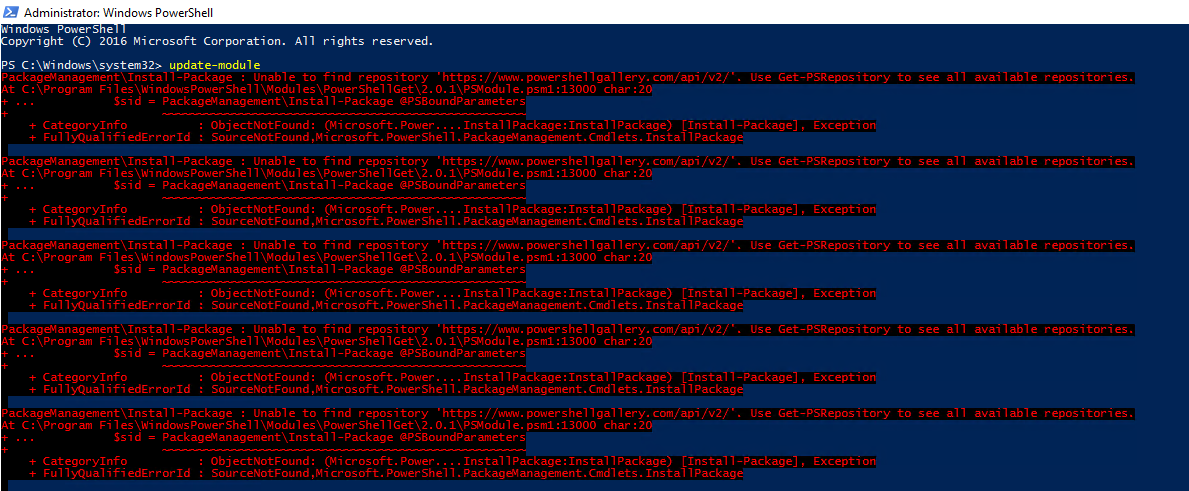
Windows PowerShell ISE starts as Administrator
However some things do not get started that way such as:
Active Directory Module for Windows PowerShell
You have to explicitly choose Run as Admin to get proper Window. And even thou you don't get the UAC prompt anymore the PowerShell module gets loaded properly with Administrator rights.
This also happens in multiple other scenarios (installing Exchange, installing Exchange updates . And because it's not visible at first sight the results are often very unpredictable.
💡 Solution
To fully disable UAC one can do this via Registry or via Local Policies interface.
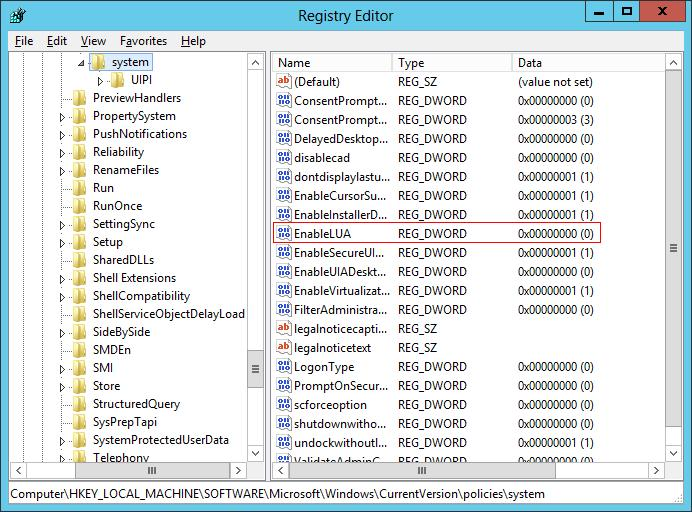
Option 1. You have the option to turn off UAC via registry by changing the DWORD „EnableLUA” from 1 to 0 in „HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system”, and doing system reboot.
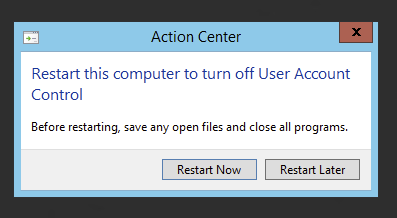
After which you will get prompted to restart computer to activate the change.
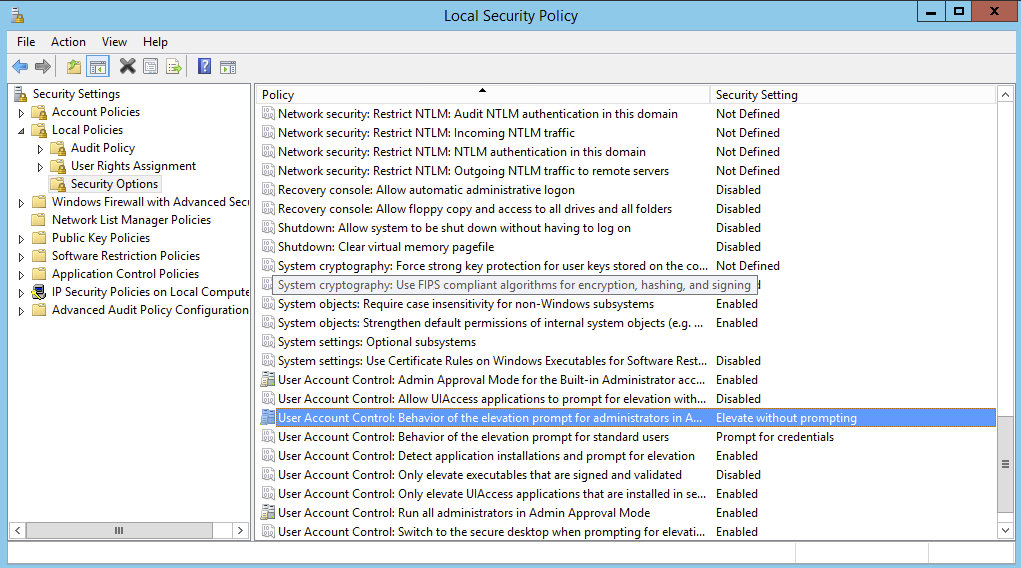
Option 2. Opening Local Security Policy (secpol.msc) and changing User Account Control: Behavior of the elevation prompt to Elevate without Prompting.
Hopefully after applying those settings the problem of weird problems coming from not Run As Admin option will be past.
🔴 Registry file to DISABLE UAC
Save file as DisableUAC.reg and run it.
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System] "ConsentPromptBehaviorAdmin"=dword:00000000 "EnableLUA"=dword:00000000
🟢 Registry file to ENABLE UAC
Save file as EnableUAC.reg and run it. Just in case you change your mind. Following reg file simply brings back default settings.
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System] "ConsentPromptBehaviorAdmin"=dword:00000005 "EnableLUA"=dword:00000001